Emerging Tech: Security — The Need for Wireless Airspace Cybersecurity
Download now▶Resources
Page 2 of 10
 Video
VideoSnippet 26: Zigbee Network Demonstration
 Video
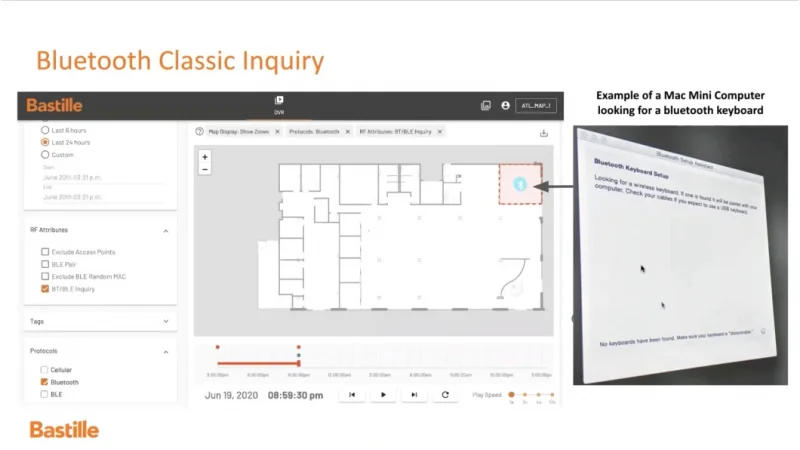
VideoSnippet 25: Demonstration of Bluetooth Classic Inquiry in Bastille Office
 Video
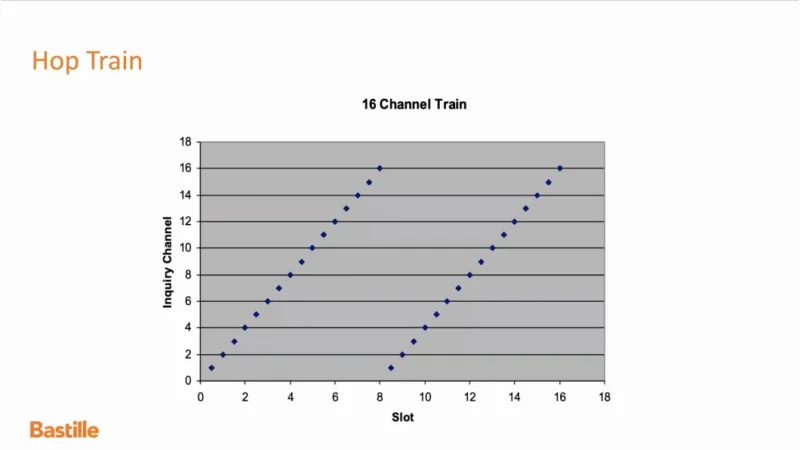
VideoSnippet 24: Bluetooth Denial of Service Attack (Bluetooth Low Energy)
 Video
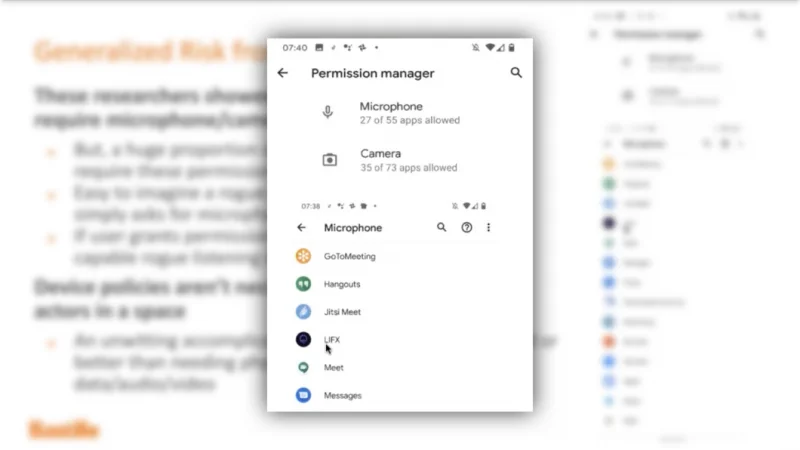
VideoSnippet 23: Malicious Applications Leveraging RC Interfaces
 Video
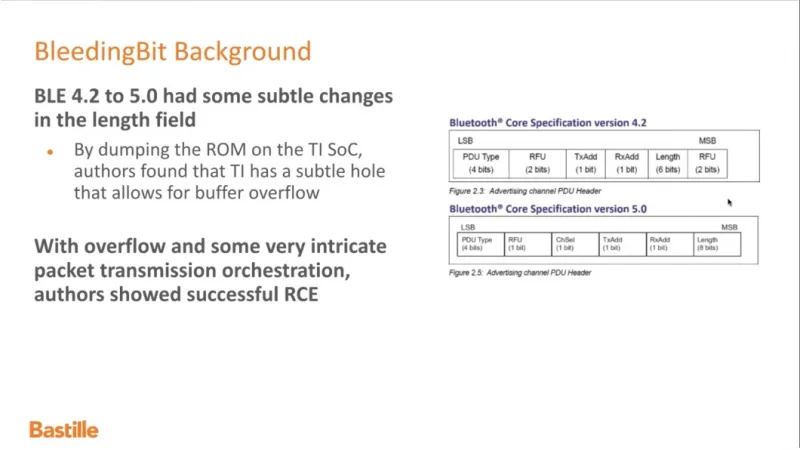
VideoSnippet 22: Bleeding Bit Attack
 Video
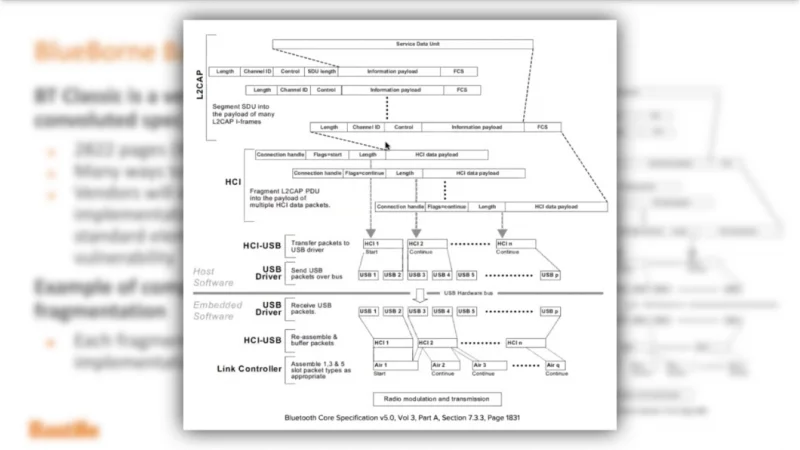
VideoSnippet 21: Blueborne Attack Linux Kernel RCE
 Video
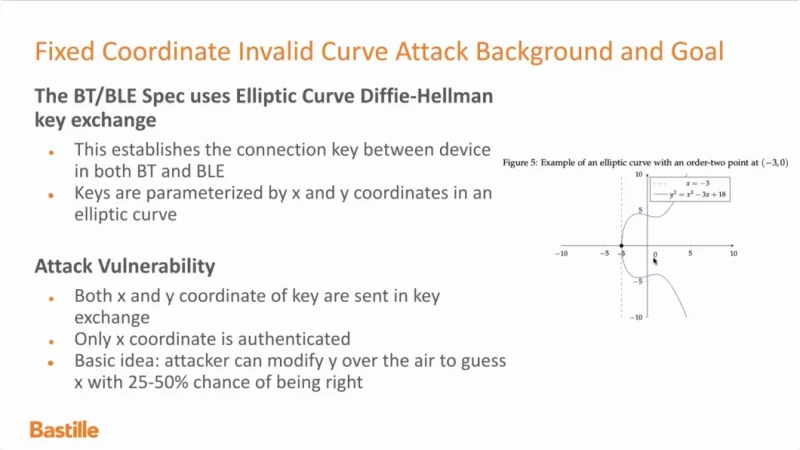
VideoSnippet 20: Fixed Coordinate Invalid Curve Attack
 Video
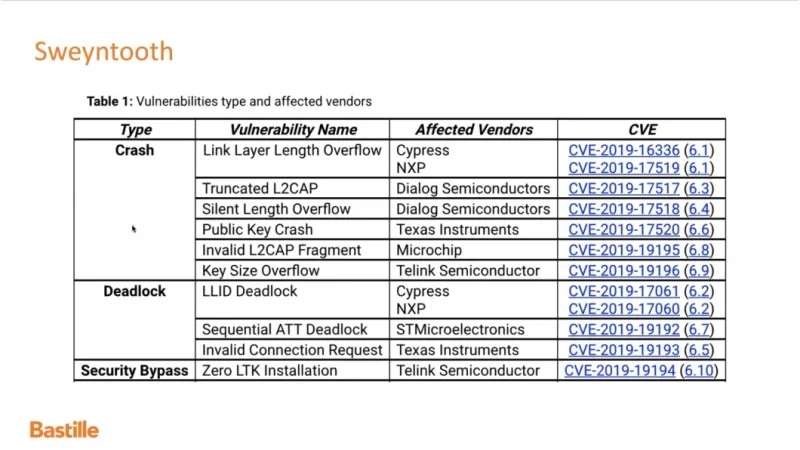
VideoSnippet 19: Sweytooth Example Attack- Sequencial ATT Deadlock
 Video
VideoSnippet 18: Sweytooth Example Attack Link Layer LLID Deadlock
 Video
VideoSnippet 17: Sweyntooth Introduction
 Video
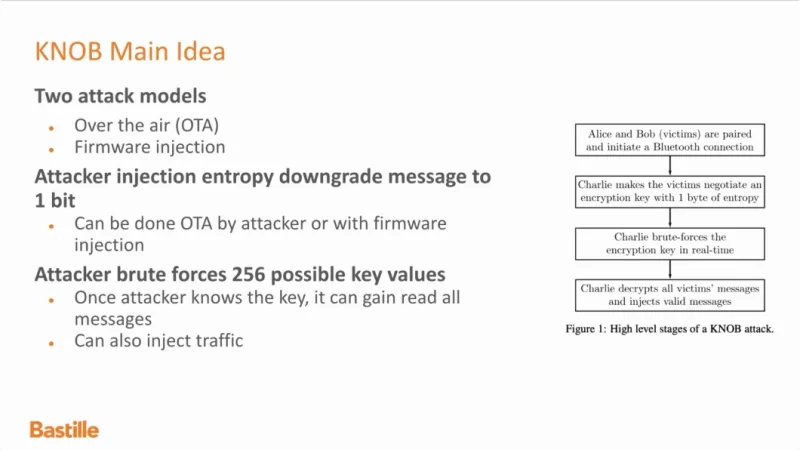
VideoSnippet 16: Key Negotiation of Bluetooth
 Video
VideoSnippet 15: Bluetooth Impersonation Attacks
 Video
VideoSnippet 14: Bluetooth Classic and Low Energy
 Video
VideoSnippet 12: Overview of Services and Products
 Video
VideoSnippet 11: Cell Phone Detection and Network Access Control
 Video
VideoSnippet 5: USB Ninja
 Video
VideoSnippet 4: Bastille Integrations with Aruba and Splunk to catch evil twin
 Video
VideoSnippet 3: Bastille Integrations
 Video
VideoSnippet 2: Introduction to O.MG Cable
 Video
VideoSnippet 1: Bastille DVR Overview
 Datasheet
DatasheetCellular & RF Based Threat Detection, Location and Alerting for the Enterprise
Close your cybersecurity gaps with AI-driven wireless visibility
See Bastille in action with a live demo from our experts in wireless threat detection.
