Spectrum monitoring has become essential to enterprise security. As organizations depend on Wi-Fi, Bluetooth, cellular networks, and IoT devices, the wireless spectrum represents both a critical resource and a vulnerable attack surface. Malicious actors increasingly exploit it through rogue devices, unauthorized access points, and covert transmissions.
To address these risks, enterprises are implementing real-time detection strategies supported by advanced technologies such as a Wireless Intrusion Detection System (WIDS). These systems continuously monitor the airspace, detect suspicious activity, and provide timely alerts to enable swift response.
This article examines the strategic importance of spectrum monitoring in protecting wireless infrastructure. It outlines the evolving threat landscape, explains why immediate detection is essential, and explores how WIDS integration strengthens data protection, regulatory compliance, and overall network resilience.
Table of Contents
What is Spectrum Monitoring and Why is it Crucial for Enterprise Security?
Spectrum monitoring is the systematic process of continuously scanning and analyzing a given radio frequency (RF) spectrum within a defined area. In contrast to traditional Wi-Fi monitoring, which is limited to identifying Wi-Fi signals, RF spectrum monitoring provides a holistic view of all wireless activity. This activity includes, but is not limited to:
- Wi-Fi
- Bluetooth and Bluetooth Low Energy (BLE)
- Cellular
- IoT protocols
- Miscellaneous wireless devices
This wireless visibility is critical for enterprise security, as it enables the detection and identification of any unauthorized or malicious wireless devices operating within the corporate wireless attack surface. In the absence of spectrum monitoring, an organization remains vulnerable to a wide array of threats that can circumvent conventional network security measures.
The Growing Wireless Threat Landscape in the Enterprise
The contemporary enterprise environment contains a high density of wireless activity. This complexity creates a growing set of security risks that extend across Wi-Fi, Bluetooth, Cellular, and IoT protocols.
- Rogue access points (Wi-Fi) remain a significant concern. Unauthorized APs, whether introduced by employees or adversaries, bypass perimeter defenses and create unsecured backdoors into enterprise networks.
- Evil twin attacks (Wi-Fi) are another growing threat. Attackers deploy fraudulent networks that mimic legitimate SSIDs. When users connect, adversaries can intercept and manipulate traffic to steal sensitive data or credentials.
- Unauthorized cellular and Bluetooth devices also introduce risk. Personal or unsanctioned devices such as smartphones and wearables can exfiltrate data or introduce malware, often operating outside Wi-Fi-focused monitoring.
- Denial-of-service (DoS) attacks target availability. Malicious actors flood the RF spectrum with interference, disrupting wireless services and interrupting business operations.
- IoT-based threats create persistent vulnerabilities. Compromised IoT devices often serve as entry points for lateral movement, data exfiltration, or botnet activity.
Without continuous spectrum monitoring, these threats remain invisible to traditional wired security controls.
Real-Time Detection of Wireless Threats: A Proactive Approach
Wireless security strategies are only effective if they enable real-time threat detection and response. Traditional security solutions that depend on periodic scanning or post-event log analysis often lack the agility to mitigate rapidly evolving wireless attacks. By the time these methods detect a threat, damage is usually already underway. Real-time detection of wireless threats facilitates the immediate identification and mitigation of security risks, thereby minimizing the potential for data loss, financial repercussions, and reputational damage. This proactive security posture is indispensable in today’s dynamic threat landscape, where adversaries continuously devise sophisticated techniques to breach corporate defenses.
How Spectrum Monitoring Enables Real-Time Threat Detection
Spectrum monitoring serves as the bedrock of a real-time wireless threat detection strategy. By continuously watching the RF spectrum, a spectrum monitoring solution can perform several critical functions:
- Establish a Baseline of Normal Wireless Activity: The system characterizes the normal wireless behavior within the environment, which allows for the rapid identification of anomalies indicative of a potential threat.
- Instantly Detect Unauthorized Devices: The appearance of a new or unauthorized device within the monitored airspace triggers an immediate alert to the security team.
- Identify Malicious Wireless Activity: The solution can recognize the signatures of common wireless attacks, such as evil twin attacks or cellular data exfiltration, and initiate immediate responses.
- Locate the Source of a Threat: Advanced spectrum monitoring solutions can precisely determine the physical location of a rogue device, enabling security personnel to neutralize the threat swiftly.
Beyond Traditional Security: The Role of Wireless Intrusion Detection Systems (WIDS)
A Wireless Intrusion Detection System (WIDS) represents a specialized security solution that extends the principles of spectrum monitoring to deliver advanced threat detection and prevention capabilities. While a standard spectrum analyzer provides visibility into the wireless signals present, a WIDS analyzes these signals in real time to identify and respond to specific, defined threats.
Legacy WIDS solutions monitor only Wi-Fi signals, leaving blind spots. Bastille redefined the category by extending detection across Wi-Fi, Bluetooth, Cellular, and IoT protocols, combined with accurate localization for incident responders, without requiring specialized knowledge in the RF spectrum or a deep understanding of wireless protocols. The solution detects and locates a broad array of wireless threats, from rogue APs and evil twins to unauthorized cellular and Bluetooth devices. For organizations with stringent security requirements, such as government agencies and large enterprises, a comprehensive Wireless Intrusion Detection System (WIDS) is an integral component of their security architecture. Such systems deliver the real-time visibility and control necessary to protect sensitive assets from a broad spectrum of wireless threats.
Benefits of a Comprehensive Spectrum Monitoring Solution
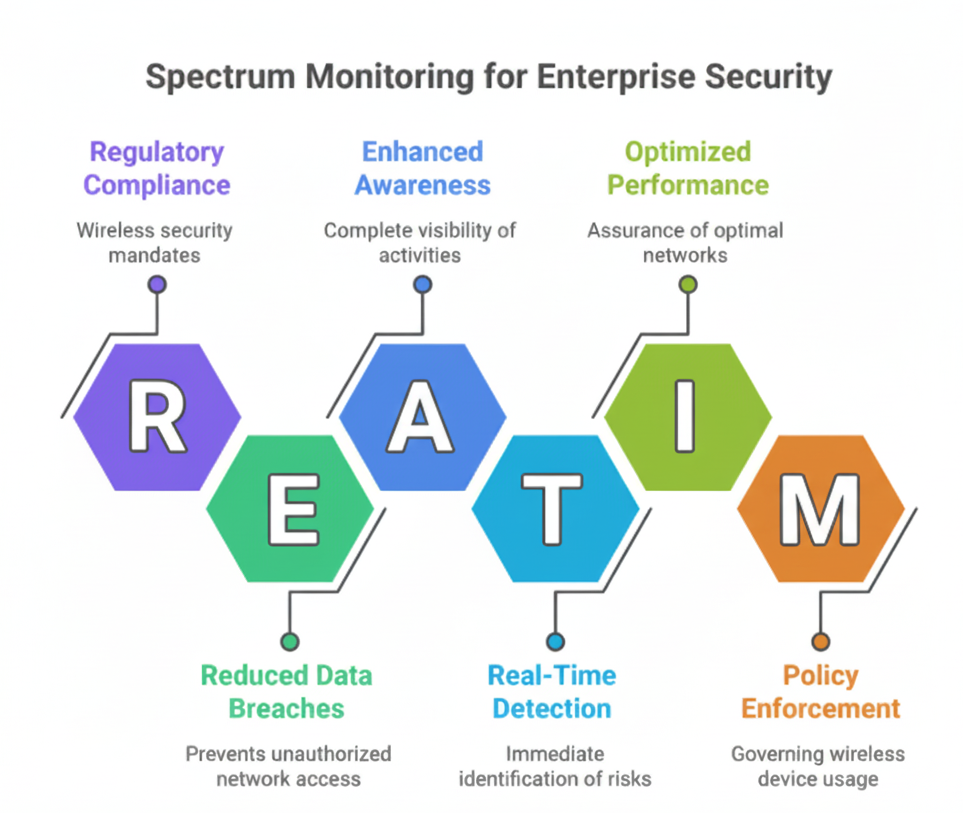
The implementation of a comprehensive spectrum monitoring solution provides measurable benefits for enterprise security, including improved security posture, enhanced situational awareness, faster incident response, reduced risk of data breaches, and stronger regulatory compliance.
- Improved Security Posture: Continuous detection and mitigation of wireless threats, reducing the likelihood of successful exploitation.
- Enhanced Situational Awareness: Full visibility into wireless activity across Wi-Fi, Bluetooth, Cellular, and IoT protocols within the enterprise environment.
- Faster Incident Response: Real-time identification and localization of rogue devices, enabling security teams to reduce Mean Time to Resolution (MTTR).
- Reduced Risk of Data Breaches: Preventing unauthorized wireless access and covert data exfiltration safeguards sensitive corporate information.
- Regulatory Compliance: Support for adherence to industry and government requirements related to wireless monitoring and data protection.
Implementing a Spectrum Monitoring Strategy
The successful implementation of a spectrum monitoring strategy requires a structured approach consisting of the following phases:
- Assess the Wireless Environment: Conduct a comprehensive inventory of all wireless networks and devices, including Wi-Fi, Bluetooth, Cellular, and IoT endpoints operating within the enterprise.
- Define Security Policies: Establish and enforce clear policies that govern the deployment and use of wireless technologies across the organization.
- Select an Appropriate Spectrum Monitoring Solution: Identify a system that provides multi-protocol coverage and aligns with the organization’s security requirements and operational constraints.
- Deploy and Configure the System: Set up and calibrate the monitoring infrastructure for RF spectrum coverage and accurate threat detection.
- Train Security Teams: Provide targeted training for analysts and incident responders to maximize the effectiveness of spectrum monitoring in daily operations.
- Continuously Monitor and Refine: Review spectrum monitoring data on an ongoing basis and update security processes and controls to adapt to evolving threats.
Frequently Asked Questions (FAQ)
What is the distinction between Wi-Fi scanning and spectrum monitoring?
Wi-Fi scanning is limited to detecting Wi-Fi signals only. Spectrum monitoring goes further by covering a broader radio frequency range, giving security teams visibility into all types of wireless activity in an environment.
Can it detect threats from cellular and Bluetooth devices?
Yes. A strong monitoring solution can uncover threats across multiple protocols, including cellular and Bluetooth, not just Wi-Fi.
How does it help mitigate insider threats?
By spotting unauthorized wireless devices inside a facility, monitoring tools can reveal attempts at data exfiltration or covert communication, both common tactics in insider threat scenarios.
Is deployment complex?
Complexity depends on the size and nature of the environment. However, modern platforms offer straightforward setup and centralized management.
How does a Wireless Intrusion Detection System (WIDS) add value?
A Wireless Intrusion Detection System (WIDS) builds on monitoring by analyzing wireless traffic in real time. It flags known threats, enables rapid response, and provides broad visibility across Wi-Fi, Bluetooth, Cellular, and IoT devices, making it a vital layer of enterprise defense.
Final Insight: Strengthening Wireless Defenses for the Long Term
Enterprises face an expanding set of risks from rogue devices, unauthorized access points, and multi-protocol wireless threats. Traditional tools cannot provide the visibility required to address these challenges. A comprehensive spectrum monitoring strategy, supported by a Wireless Intrusion Detection System, delivers the real-time detection and control necessary to secure enterprise airspace. Bastille’s WIDS solution provides full-spectrum monitoring, precise localization, and integration with existing security operations, enabling organizations to maintain compliance and resilience against evolving wireless threats.



