Many organizations lack visibility into the wireless activity inside their secure facilities. This blind spot allows threats to persist undetected, making insider risks one of the most complex challenges for enterprise security. While wired networks and endpoints are well protected, the radio frequency (RF) spectrum often remains unmonitored. This gap creates opportunities for insiders, whether malicious, negligent, or compromised, to bypass conventional defenses. Effective Insider Threat Detection relies on extending security into the wireless domain with continuous monitoring of Wi-Fi, Bluetooth, Cellular, and IoT protocols.
For organizations governed by frameworks such as the NIST Risk Management Framework (RMF), CNSSI 1253, and DoDI 8500.01, wireless visibility is not optional. It is essential for mission assurance and compliance.
This guide presents a structured framework for detecting and preventing insider threats in wireless networks.
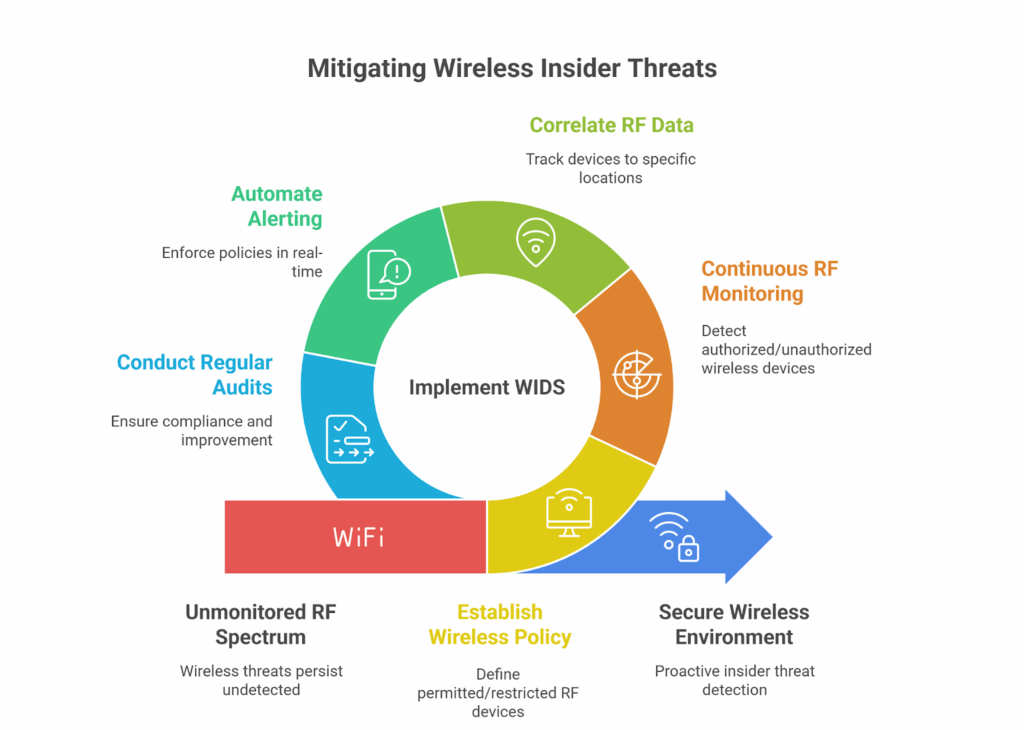
Table of Contents
Understanding the Scope of Wireless Insider Threats
An insider threat originates from an individual with authorized access who compromises information security, either intentionally or unintentionally. In wireless environments, these threats emerge through RF-enabled devices and can be classified as follows:
Malicious Insider Threats: Individuals who deliberately exploit access to cause harm. A malicious insider may use a personal cellular device to photograph sensitive documents, deploy a Bluetooth-based keystroke logger, leverage a WiFi Pineapple to spoof trusted networks, connect a wireless headset as a covert listening device, or introduce a USB Ninja Cable for covert wireless access.
Negligent Insider Threats: Individuals who unintentionally create risk through carelessness or lack of awareness. For example, an employee carrying a smartwatch with an active cellular connection into a Sensitive Compartmented Information Facility (SCIF) introduces an unauthorized RF transmission channel, violating policy and creating a potential vector for data exfiltration or eavesdropping.
Compromised Insider Threats: Individuals with devices or credentials that external actors have taken over. A compromised laptop infected with malware may activate Bluetooth or Wi-Fi functions to establish covert communication channels, bypassing secured corporate networks. In such cases, the employee becomes an unwitting participant in the breach.
Detecting these threats requires visibility across the full range of RF protocols, including Wi-Fi, Bluetooth, Cellular, and IoT.
The Limitations of Traditional Security in Detecting Wireless Insider Threats
Conventional cybersecurity infrastructure monitors and controls data flow across wired networks. Firewalls, Intrusion Prevention Systems (IPS), and endpoint security solutions remain essential, but they share a critical limitation: a lack of visibility into the RF spectrum.
Wired threats are comparatively easier to detect because they generate logs, trigger alerts, and are traceable through packet captures and flow analysis. Attempts to exfiltrate data over the corporate LAN usually activate multiple alarms. Wireless insider threats, by contrast, operate outside these defenses. Devices that do not connect to the wired or corporate Wi-Fi network remain invisible to traditional tools.
Examples include:
Air-Gapped Network Breach: An insider uses a personal smartphone as a cellular hotspot to bridge an air-gapped network. This tactic bypasses the firewall entirely, giving external actors direct access to critical infrastructure.
Covert Data Exfiltration: An employee leverages a phone’s cellular data connection to upload sensitive files. Because the transfer occurs outside the corporate network, neither endpoint controls nor network security tools detect the activity.
Unauthorized Device Communication: Two Bluetooth-enabled devices establish a peer-to-peer channel within the facility. This communication path operates independently of corporate IT infrastructure, making it invisible to network monitoring systems.
These scenarios highlight a fundamental limitation: conventional defenses cannot reliably detect or control wireless insider threats. Therefore, effective insider threat detection requires persistent visibility into the RF spectrum across all wireless protocols.
A Step-by-Step Framework for Insider Threat Detection in Wireless Networks
A proactive strategy for mitigating wireless insider threats requires a structured, multi-layered framework. The following steps outline the core components of an effective detection and prevention program:
Step 1: Establish a Comprehensive Wireless Device Policy
A clear wireless device policy is the foundation of insider threat defense. It should align with regulatory requirements such as NIST SP 800-53 and define which RF-emitting devices are permitted, restricted, or prohibited in specific areas. Policies must address all major protocols, including Wi-Fi, Bluetooth, and Cellular, and be communicated across the organization to maintain consistent compliance.
Step 2: Implement Continuous RF Monitoring
Policies are effective only when enforced. A Wireless Intrusion Detection System (WIDS) delivers continuous RF monitoring, detecting and classifying both authorized and unauthorized devices from everyday smartphones to covert tools. This persistent visibility builds a live inventory of RF activity, forming the baseline for detection and response.
Step 3: Correlate RF Data with Physical Location
Identifying an unauthorized device is insufficient without knowing where it is. Advanced WIDS solutions correlate RF signals with physical locations, enabling device tracking to the floor, room, or desk level. This precise localization supports rapid incident response, forensic investigations, and enforcement of policies in high-security areas such as SCIFs or data centers.
Step 4: Automate Alerting and Response Protocols
Manual monitoring is not scalable. Effective insider threat programs integrate automation to enforce policies in real time. When WIDS detects a violation, such as a cellular signal in a restricted zone, it generates an alert instantly. Integration with Security Information and Event Management (SIEM) or orchestration platforms enables security teams to respond immediately, reducing dwell time and minimizing risk.
Step 5: Conduct Regular Audits and Reporting for Compliance
Auditing and reporting are essential for both compliance and continuous improvement. A robust WIDS generates comprehensive records of all RF activity, policy violations, and responses. These reports support regulatory frameworks such as the NIST Risk Management Framework (RMF) and CNSSI 1253, while also providing actionable insights to refine wireless policies and strengthen long-term security posture.
Case Insight: Detecting an Unauthorized Smartwatch in a Sensitive Compartmented Information Facility (SCIF)
Scenario: In a government Sensitive Compartmented Information Facility (SCIF), policy prohibits devices with cellular or Wi-Fi transmission capabilities to prevent unauthorized data exfiltration.
Threat: An employee inadvertently wears a smartwatch with an active LTE connection into the secure facility. This situation creates a negligent insider threat by introducing an unmonitored communication channel to the outside environment.
Detection: A Wireless Intrusion Detection System (WIDS) monitoring the RF spectrum identifies the unauthorized LTE signal, even though the device does not connect to the corporate network.
Response: The WIDS calculates the device’s location to a specific desk and sends a real-time alert to the security team. Security personnel address the incident discreetly, maintaining policy compliance while reducing potential risk.
Outcome: The security team eliminates the potential data exfiltration channel, enforces policy, and logs a detailed incident record for compliance reporting and auditing.
The Role of a Wireless Intrusion Detection System (WIDS) in Preventing Insider Threats
Bastille’s Wireless Intrusion Detection System (WIDS) is the core technology enterprises rely on for wireless insider threat detection. Traditional WIDS solutions focused only on Wi-Fi, leaving blind spots across other protocols. In contrast, a comprehensive WIDS delivers broad-spectrum RF visibility, helping minimize the chance that unauthorized devices or signals go undetected.
Bastille’s enterprise and government-grade WIDS delivers the advanced capabilities required to defend against wireless insider threats, without requiring specialized knowledge in the RF spectrum or a deep understanding of wireless protocols. Its key functions align directly with the essential steps of detection and prevention:
Comprehensive Visibility: Persistent monitoring across the RF spectrum, detecting and classifying devices using Wi-Fi, Bluetooth, Bluetooth Low Energy, Cellular, and IoT protocols. This range of protocols eliminates blind spots that conventional tools miss.
Precise Locationing: Real-time localization of RF-emitting devices displayed on floor maps. This capability gives security teams actionable intelligence to locate and neutralize threats quickly and accurately.
Automated Policy Enforcement: Organizations can define and enforce granular wireless security policies. Bastille’s WIDS automatically identifies prohibited devices such as cellular phones in no-carry zones and generates instant alerts for rapid response.
Forensic and Compliance Reporting: The solution logs all RF activity, producing a detailed, tamper-proof record for forensic analysis and compliance audits. This function supports adherence to frameworks such as NIST SP 800-53 and CNSSI 1253.
By deploying a comprehensive WIDS, organizations close a critical visibility gap in their security posture. The solution enables a proactive approach to insider threat detection, addressing the risks posed by the growing number of wireless devices in modern enterprises and government environments.
Frequently Asked Questions (FAQ) about Wireless Insider Threat Detection
What is the difference between a malicious and a negligent insider threat?
A malicious insider deliberately seeks to cause harm, such as stealing data with a personal device. A negligent insider unintentionally creates risk, for example, by bringing a smartwatch with cellular capability into a restricted area. The intent differs, but both can jeopardize security.
How does a comprehensive WIDS differ from a traditional Wi-Fi IDS?
A traditional Wi-Fi IDS monitors only 802.11 protocols and misses threats from Cellular, Bluetooth, and IoT devices. A comprehensive WIDS, such as Bastille, provides broad-spectrum RF monitoring, giving visibility into all wireless activity.
Which compliance frameworks address wireless security?
Frameworks that mandate or recommend wireless security include the NIST Risk Management Framework (RMF), NIST SP 800-53 (controls AC-19, RA-3, SI-4), CNSSI 1253, and Department of Defense Instruction (DoDI) 8500.01. These require monitoring and controlling wireless devices within facilities.
Can insiders exfiltrate data without connecting to the corporate network?
Yes. Insiders can use independent cellular connections, such as hotspots, or peer-to-peer links like Bluetooth to transfer data. These connections bypass firewalls, DLP tools, and other network-based defenses.
Strengthening Wireless Insider Threat Defense
The rapid growth of wireless-enabled devices has turned the RF spectrum into a significant channel for insider threats. Unlike traditional IT risks, these threats often bypass wired defenses, making targeted spectrum monitoring essential.
Bastille’s Wireless Intrusion Detection System (WIDS) provides enterprises with continuous visibility into the RF environment. It enables the detection, location, and mitigation of unauthorized devices before they can cause a breach. By combining persistent monitoring with precise location tracking, Bastille equips security teams to respond quickly, reduce the risk of data exfiltration, and support compliance with regulatory requirements, without requiring specialized knowledge in the RF spectrum or a deep understanding of wireless protocols.
As organizations adapt to increasingly complex wireless environments, proactive Insider Threat Detection has become a critical component of enterprise security. A comprehensive Insider Threat Detection approach, supported by WIDS, protects sensitive or privileged assets and strengthens long-term security resilience.



