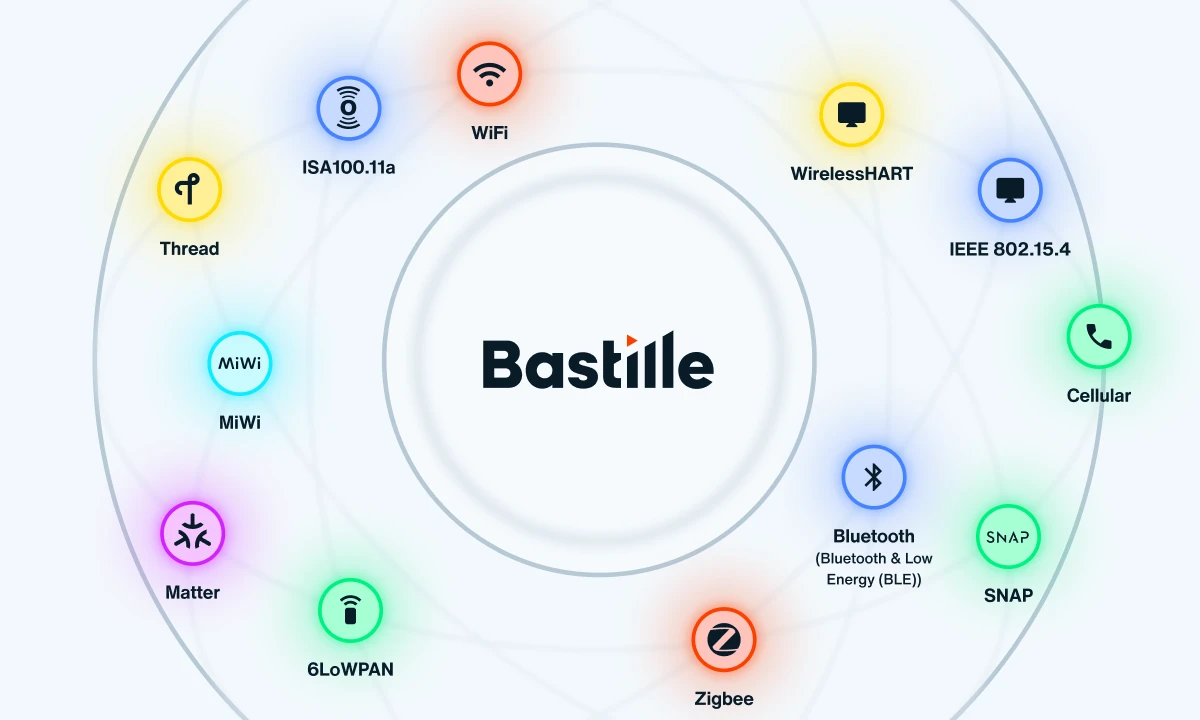
One platform for complete wireless compliance
Maintain an audit-ready, evolving record of the efforts your organization makes to protect sensitive data and processes. Bastille makes it easy to understand your wireless landscape, share information across security and risk management teams, and provide reports to auditors from one place.