Cyber-physical convergence in operational technology (OT)
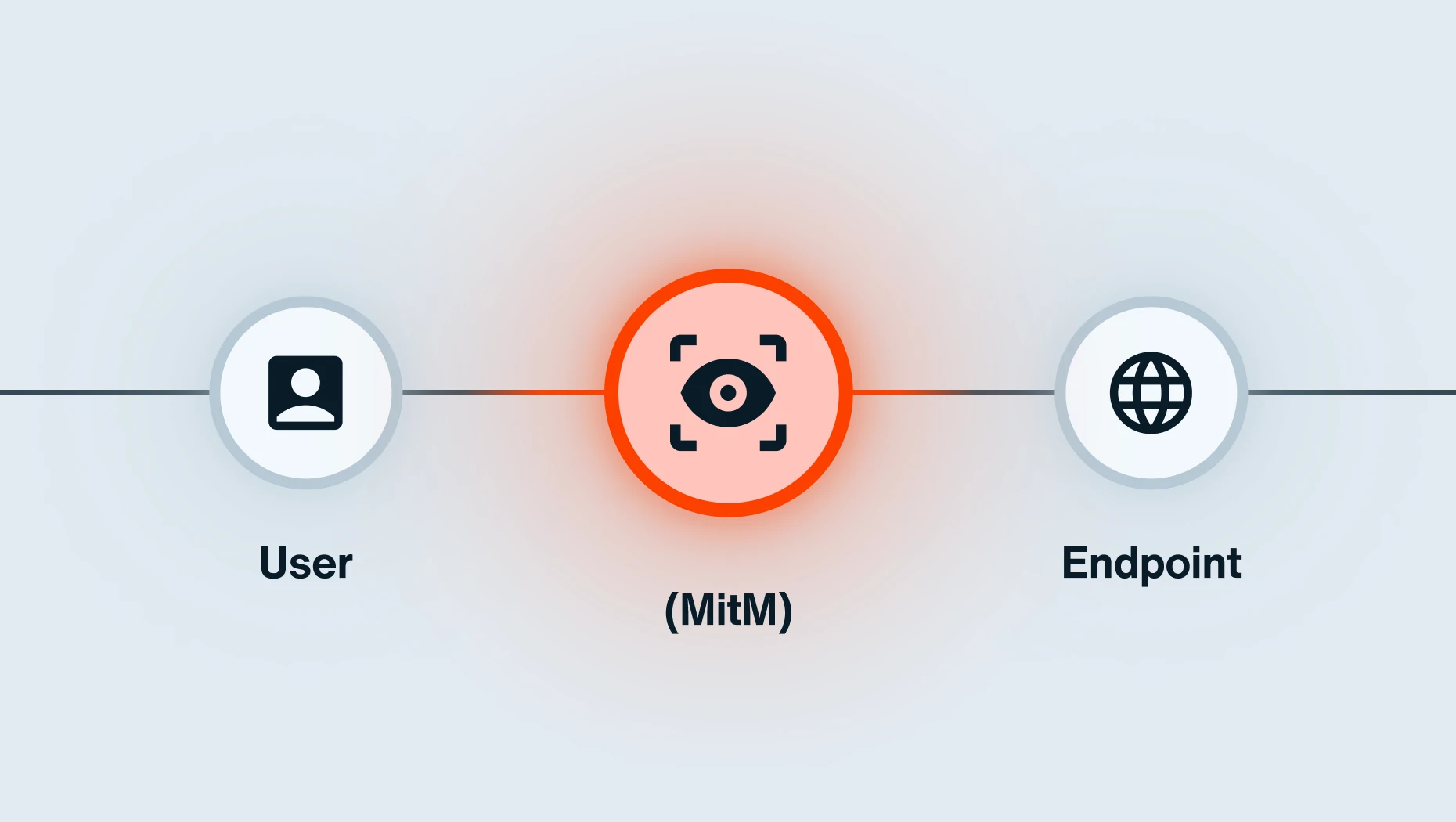
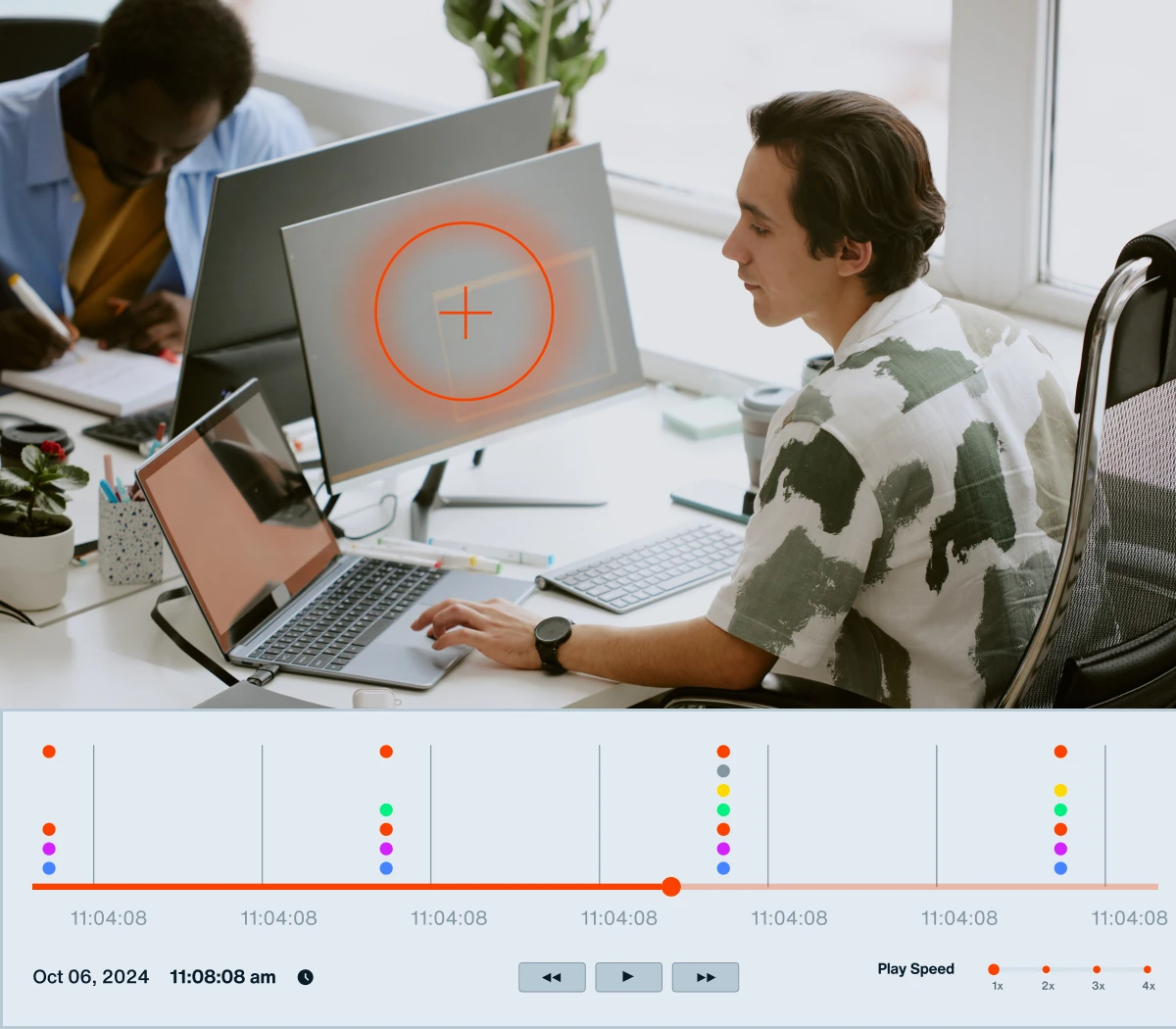
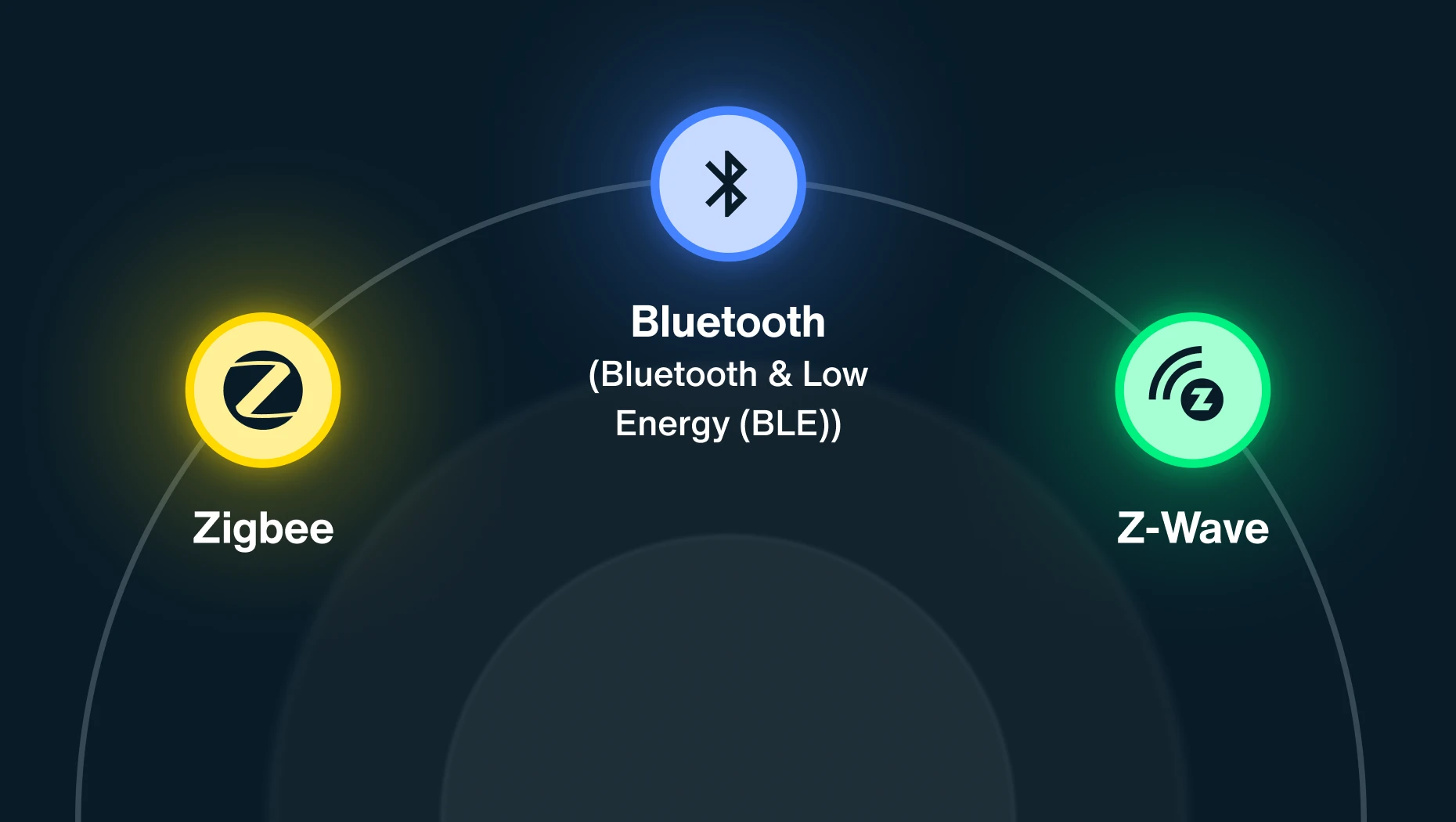
ICS/OT networks are no longer isolated from the vast cloud ecosystems that many bad actors target, instead connected to distributed networks via wireless protocols like Zigbee, Z-Wave, and LoRaWAN. To minimize this extensive attack surface, OT leaders must continuously scan their airspace for wireless threats.