
Download Now
Securing classified areas and Sensitive Compartmented Information Facilities (SCIFs) requires a suite of security tools, protocols, and personnel working together. Learn how Bastille’s Wireless Airspace Defense solution is a critical part of any strategy for securing sensitive or classified information.
Mission Security Is Critical
Securing classified areas and Sensitive Compartmented Information Facilities (SCIFs) requires a suite of security tools, protocols, and personnel to ensure the broadest and most comprehensive solution is in place. Each mission has different security requirements, the strictest of which include securing locations from wireless threats.
The world has moved on from a simple 100% wireless device exclusion policy. Wireless electronic device policy has evolved to keep pace with employment law, attract and retain talent, and embrace sensor-rich mission support technologies. Today, allowing personal medical devices, performance-enhancing wearables, and supporting a broader personnel profile is a reality. An intelligent wireless threat security system is more than device detection; it must support rapid geolocation, device assessment, and simplified adjudication workflows.
Physical Security Has Limits
Physical security of classified areas is a well-refined practice involving identity scanners, physical blockades, trained guards, motion detectors, and comprehensive camera systems. It focuses entirely on what can be seen and touched and will always fail to detect invisible, wireless threats.
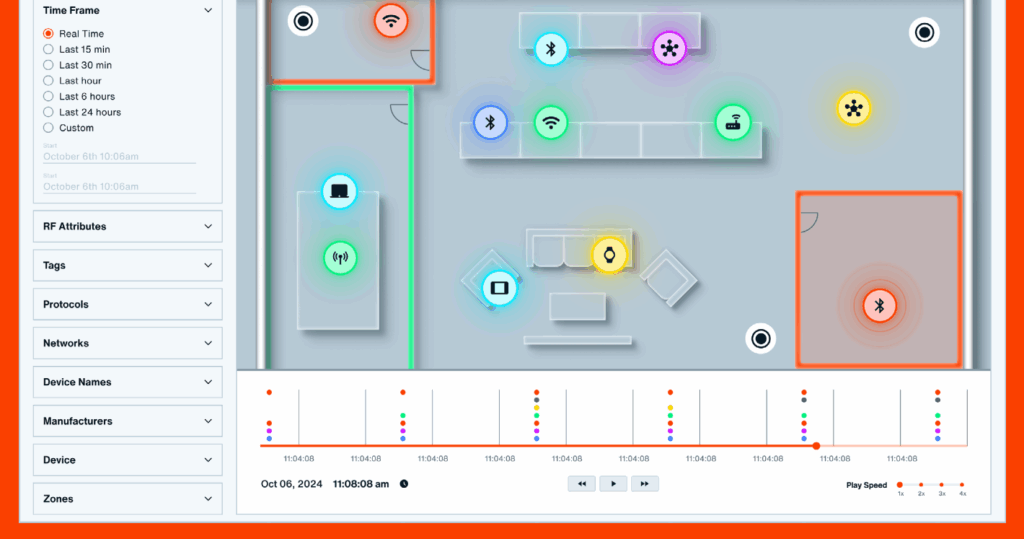
Wireless Airspace Defense, by contrast, focuses on identifying and locating the invisible threats present in today’s classified facilities.
Bastille’s solution can ensure your classified area is continuously monitored for wireless activity and identify threats before they reach the sensitive data your mission is handling.
Wireless Threats
Wireless threats, like network-borne vulnerabilities and malware, are evolving rapidly. However, they have a distinct advantage over network-centric attacks: They are not detectable on managed networks. Wireless threats can exfiltrate data out-of-band from even the most complex firewall, intrusion detection, and malware scanning systems on a physical network. You must continuously monitor for wireless threat activity to ensure your classified space is free of unknown wireless threats.
Wireless threats manifest themselves in forms such as:
- Cellular voice, data and video ex-fil devices, which can bridge physical networks
- Rogue Wi-Fi access points and data ex-fil devices
- Rogue video and still-image cameras
- Bluetooth-based data harvesting devices
- Industrial Control System jammers, blockers and signal interfering devices
These threats can compromise the security of the spaces where you hold sensitive discussions, process critical information, or have compliance obligations regarding the security of the wireless airspace.
Cellular Phones
Most SCIFs have a set of lockers outside, and everyone entering the SCIF knows they should have left their phone in their vehicle or in one of those lockers. And yet, many of us have been in a classified meeting when we heard a phone ring! Was that phone also compromised by spyware, unbeknownst to the user? Cell phones are notoriously hard to detect just by their cellular signal. The cellular signals phones emit are just not as “chatty” as expected. Bastille has the unique ability to locate cell phones just by their cellular signal, separate multiple such phones, and put an accurate location dot on a floor plan map to tell you the exact whereabouts of each phone.
Whether a person maliciously or accidentally brought a cell phone into your SCIF is secondary to your need to know precisely and immediately where it is, where it’s been, and as much attribute data about the device as possible.
Threats Are Evasive
Wireless devices used for eavesdropping or data exfiltration would be ineffective if they were easy to find. They often attempt to avoid detection by transmitting during busy times (to blend in) or off-hours (fewer observers). A continuous monitoring wireless TSCM system, like Bastille, will detect threat devices whenever they transmit.

