
Download Now
Cellular & RF Threat Remediation
Bastille provides corporations and agencies with comprehensive RF and cellular threat detection capabilities using Software Defined Radio technology that passively monitors the entire radio spectrum from 60 MHz to 6 GHz. The system continuously scans facilities to detect, locate, and identify wireless devices including cellular phones, Wi-Fi, Bluetooth, and IoT devices, providing accurate real-time location mapping and threat analysis.
The platform operates through a three-stage process: Discover (detecting and locating wireless emitters with precise floor plan mapping), Analyze (classifying devices and creating rule-based alerts that integrate with incident response systems), and Act (enabling investigation and resolution through device information analysis and forensic DVR capabilities). Bastille’s patented technology digitally demodulates protocols to differentiate individual devices, unlike competing solutions that only provide energy heatmaps.
Bastille integrates seamlessly with existing security infrastructure including SIEM systems, MDM platforms, network access control systems, and physical security equipment. The system can automatically adjudicate authorized devices, trigger alerts through multiple channels, and coordinate with other security tools for automated threat response. It supports both on-premise and cloud deployments, scaling from single rooms to global enterprise installations.
The solution addresses critical security vulnerabilities including cellular intrusion detection, rogue access points, Bluetooth data exfiltration, surveillance devices, and vulnerable IoT equipment. Available in three configurations (Enterprise for permanent installations, Express XLE for medium deployments, and Express for tactical rapid deployment), Bastille provides organizations with visibility into wireless threats that traditional network security cannot detect, as over 70% of connected devices now use RF and cellular protocols that bypass conventional firewalls.
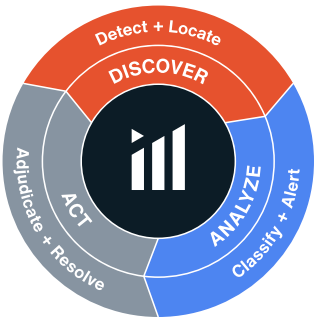
Discover: Detect and Locate
The core and multi-patented technology of our sensor arrays and analytics continuously scans your airspace and detect wireless emitters, digitally demodulate those signals, identify protocols and individual unique devices. This allows Bastille to put an accurate dot on a floor plan map of your facility to show the location of each individual device.
Analyze: Classify and Alert
Bastille provides context information about the devices it locates. This allows you to tell whether the device that is represented by the dot is connected with other devices, what kind of data it is streaming, or if it’s being actively attacked in certain cases. Rule-based alerts can be established that interact with your incident response workflow. Using integrations, Bastille alerts can be used to send emails, text message, phone calls, or to instantiate tickets in an external incident response system like PagerDuty, ServiceNow, or Lenel OnGuard.
Act: Adjudicate and Resolve
You can undertake various levels of investigation. For example, if you click through a Bluetooth device, Bastille might be able to tell you that it’s a Sony device and give you a model number that corresponds to a television. With that information, you might infer that somebody has just put a television in your space and it has an active Bluetooth connection. From there, you may choose to physically intervene to remove the device, or decide to use one of the Bastille integrations to your other network systems to disable the device automatically. Similarly, you can use Bastille’s DVR feature to go back in time and see a given device’s presence and location history. Through this forensic analysis, it may become clear that the device has been in or near restricted areas, or that the device has been present during off-business hours in a way that is indicative of involvement in a malicious event.
