The plain-text public advisories can be found at CERT/CC VU#981271.
Remediation
– Immediately disconnect all affected USB dongles, and use wired keyboards and mice instead.
– If you are using affected Logitech or ‘Lenovo 500’ devices, please update your firmware by referring to the appropriate instructions (see appropriate Vendor Response links above).
Dongles from other vendors were not found to support upgrading of firmware, so it does not appear possible to patch them. Therefore it is recommended that users contact their preferred vendor and inquire into which models are not vulnerable for future purchases.
Tools
The Bastille Threat Research Team is releasing free, open source tools to enable interested parties to discover wireless mice and keyboards that may be vulnerable to MouseJack.
Please refer to: https://github.com/rfstorm/mousejack
A Python-based sniffer is available, and will output raw frames to the console:

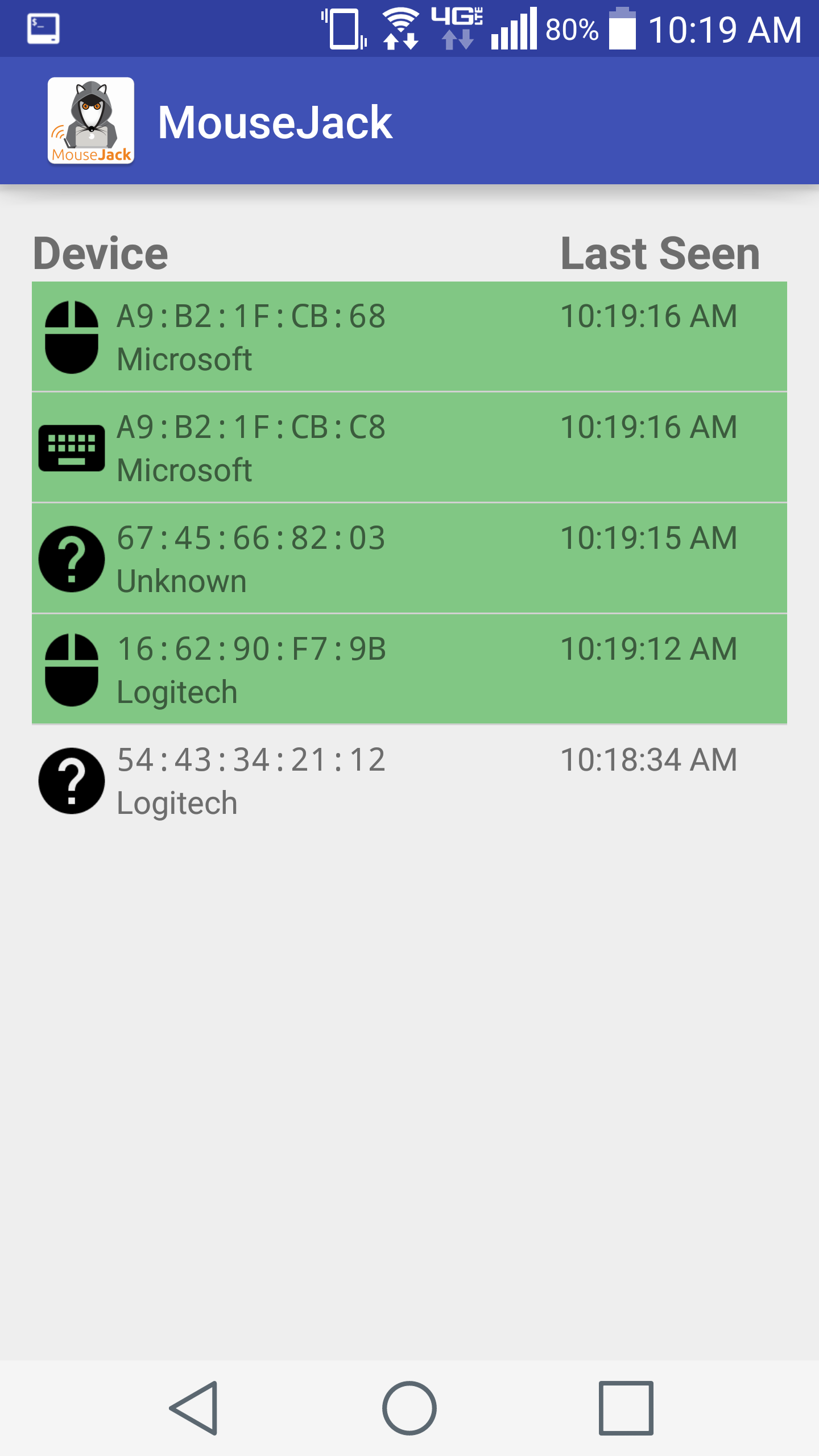
An Android application for sniffing has been developed and is now available:
T I M E L I N E
| Date | Events |
|---|---|
| 2015 November 24th | Initial vendor disclosure |
| 2016 January 11th | CERT/CC advisory sent |
| 2016 February 23rd | Public disclosure |
| 2016 February 24th | CERT/CC releases advisoriesAdded Logitech & Lenovo firmware update links |
| 2016 February 25th | Uploaded statement from Dell |

