
Protecting secure facilities is more complex than ever in today’s threat landscape. Many organizations, particularly those in the defense and federal sectors, enforce strict policies prohibiting radio frequency (RF) devices within their walls.
These prohibitions are not without reason. RF devices pose significant security risks, including data exfiltration, unauthorized access, and the revelation of critical operational tactics to adversaries.
Monitoring the RF environment is essential to mitigate these risks. However, the question arises: How can organizations monitor for RF threats without inadvertently compromising their security? The answer lies in passive RF monitoring.
Why Passive RF Monitoring Is Essential
Passive RF monitoring allows organizations to maintain covert surveillance of their RF environment without alerting adversaries to the presence of security measures. This approach has several advantages, making it an ideal method for securing sensitive facilities. The following are the top three reasons why passive RF monitoring is indispensable.
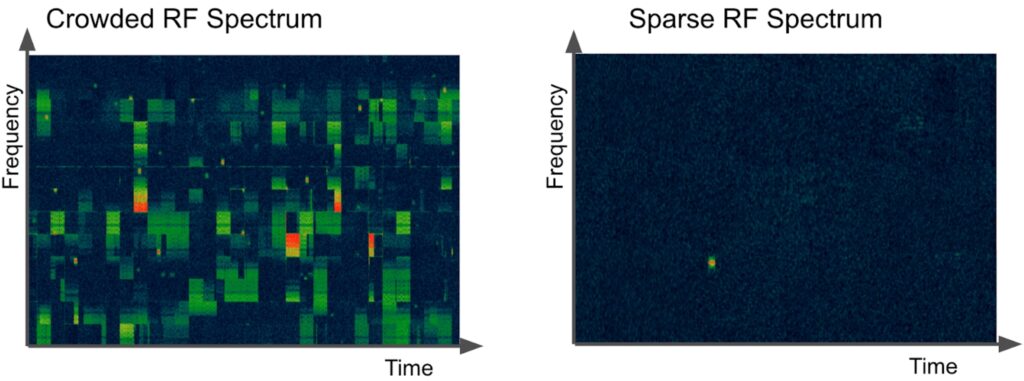
1. Visibility Issues in a Crowded RF Spectrum
Secure environments must contend with a significant challenge: the RF spectrum is increasingly crowded with transmissions from both authorized and unauthorized devices.
Consumer electronics like Bluetooth devices, Wi-Fi access points, and portable devices like phones, laptops, wireless peripherals, and others emit RF signals that can clutter the spectrum, providing adversaries ample cover to hide their malicious signals.
In such environments, detecting unauthorized or rogue transmissions is akin to finding a needle in a haystack, and pursuing an active RF monitoring solution (one that emits its own RF signals) will add to the clutter. Security teams can filter through the noise and efficiently pinpoint illicit signals by leveraging passive RF monitoring. For example, Bastille’s 100% passive sensors can detect RF emissions without adding to the noise, giving organizations a clearer view of potential threats.
2. Operational Security (OPSEC) Considerations
Active Wireless Intrusion Detection Systems (WIDS) rely on emitting signals to scan the RF environment. This approach compromises operational security (OPSEC), as adversaries can detect these transmissions. Once aware of the system’s presence, they can:
- Deploy countermeasures: to evade detection.
- Identify gaps: in coverage, knowing where the system does or does not have detection coverage.
- Monitor for changes: such as when WIDS transmissions cease – and exploit potential coverage gaps.
- Home in on the facility: using WIDS signals as beacons for drone or targeted attacks.
In contrast, passive RF monitoring systems do not emit any signals. As a result, adversaries remain entirely unaware of the security infrastructure in place. This stealth approach is crucial in maintaining OPSEC, particularly in environments vulnerable to sophisticated adversaries capable of exploiting even the most minor security weaknesses.
Bastille’s Radio Frequency Direction Finding technology takes this further by detecting RF devices and determining their physical location within a facility without emitting detectable signals.
3. Compliance with Security Policies and Guidelines
Federal policies and industry guidelines increasingly demand passive-only RF monitoring in secure environments. The National Information Assurance Partnership (NIAP) outlines in its Wireless Intrusion Detection System (WIDS) Protection Profile that passive scanning is the preferred approach for secure facilities. Passive systems ensure that the RF spectrum remains clear of extraneous emissions, thereby reducing potential cover for malicious actors.
Active systems, by contrast, introduce additional RF traffic, which can crowd the spectrum and inadvertently aid adversaries in concealing their transmissions. For instance, active systems prompt nearby devices to respond, increasing the volume of transmissions in the spectrum. This increased clutter in the RF spectrum makes it easier for rogue devices to blend in and mask their activities.
Bastille’s entirely passive, software-defined radio (SDR) systems ensure compliance with these strict security policies, providing robust wireless intrusion detection without contributing to spectrum clutter.
The Technological Advantage: From Legacy Systems to SDR
Historically, monitoring Bluetooth and Bluetooth Low Energy (BLE) devices posed a unique challenge. Legacy Wireless Intrusion Detection Systems (WIDS) relied on active inquiry packets to identify nearby devices. This method required the system to transmit RF signals to identify local devices. While effective in detecting a tiny subset of devices, this approach had two critical flaws:
- It required active transmissions, violating the principle of passive monitoring.
- It only detected unpaired devices that responded to inquiry packets, missing many Bluetooth/BLE devices altogether. This limitation is significant as most (if not all) data exfiltration exploits happen over a data connection between two or more paired devices.
Bastille’s modern SDR-based technology overcomes these limitations. Unlike legacy systems, Bastille’s solution can detect all Bluetooth and BLE devices in the vicinity, regardless of their connection state (unpaired, paired, transmitting data), without sending inquiry packets. The system’s ability to monitor inquiry packets from rogue devices or legacy systems adds a layer of protection, ensuring comprehensive visibility in the RF environment.
Real-World Example
A recent pilot project at a secure facility demonstrated Bastille’s solution and the advantages of its completely passive SDR technology. In the pilot, Bastille’s system detected a staggering 4.8 million Bluetooth inquiry packets per hour, far beyond what usually occurs in a secure facility. This volume suggested that legacy Bluetooth sensors or security systems actively transmit inquiry packets and add clutter to the very RF spectrum it is supposed to monitor.
Bastille’s system identified the location of these rogue emitters within the facility and provided detailed analytics on the volume of inquiry packets over time. The data showed that the emitters were turned off for about a week and then turned back on again. An operator can use this time and position data to verify that these emissions came from a legacy active Bluetooth detection system.
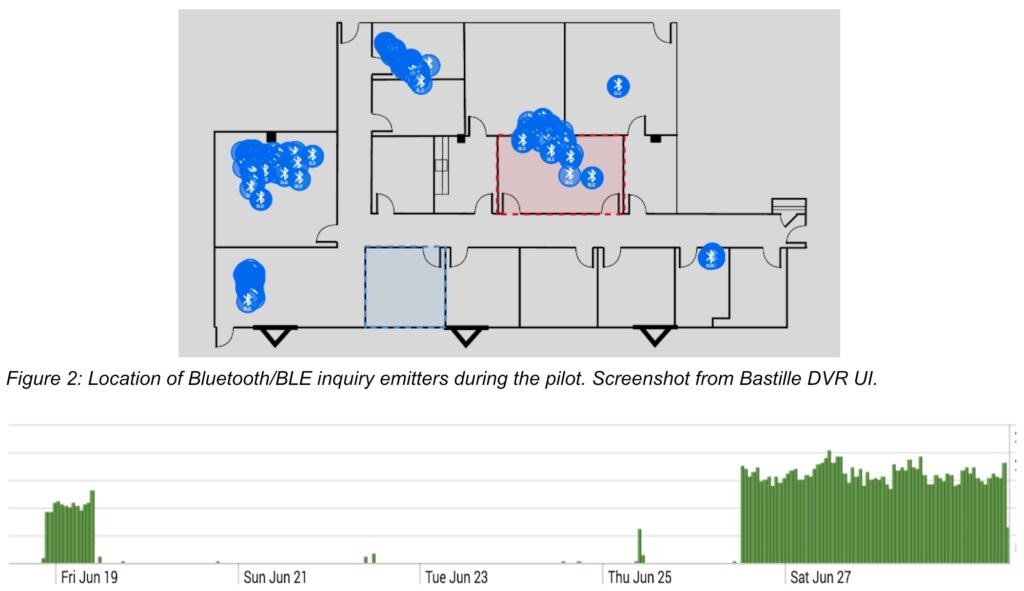
The data gathered during the facility’s pilot project highlights the limitations of legacy Bluetooth detection systems. Active transmissions, such as those produced by inquiry packets, can create a noisy RF environment that is difficult to monitor. By contrast, passive systems like Bastille’s provide real-time visibility into all Bluetooth and BLE activity, allowing for early detection of potential security threats.
The Future of RF Monitoring: Passive, Comprehensive, and Secure
As wireless threats evolve, so must the technologies used to defend against them. Passive RF monitoring, powered by SDR technology, represents the future of secure facility protection. By eliminating the need for active transmissions, passive systems maintain operational security, reduce spectrum crowding, and provide comprehensive visibility into RF devices.
Bastille’s innovative approach to entirely passive monitoring ensures that organizations can stay ahead of adversaries, protect sensitive data, and maintain compliance with federal guidelines. Whether it’s preventing data exfiltration, defending against rogue devices, or guarding against inadvertent operational disclosures, passive RF monitoring is a critical component of modern cybersecurity strategies.
Bastille is leading this evolution, offering compliant and future-proof solutions. With capabilities to monitor, detect, and respond to RF threats while remaining completely passive and never broadcasting its presence, Bastille’s continuous monitoring technology helps organizations maintain control over their RF environment.


