Emerging Tech: Security — The Need for Wireless Airspace Cybersecurity
Download now▶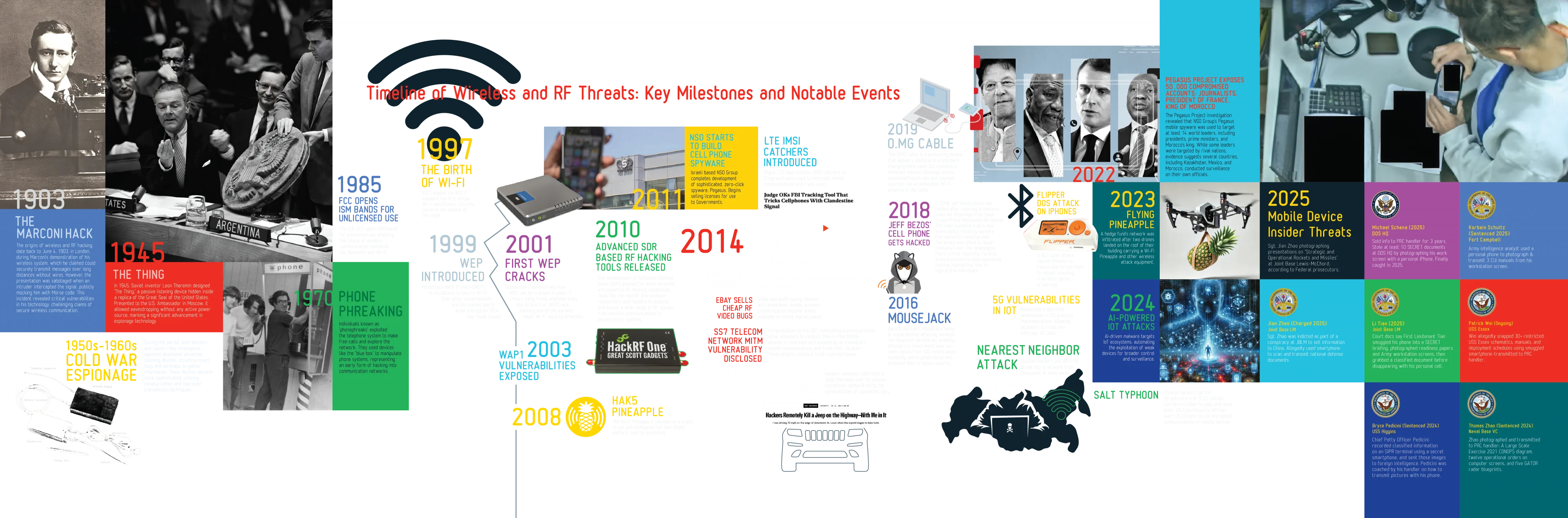
Timeline of Wireless and RF Threats: Key Milestones and Notable Events
2025
Researchers Shut Down ICS Electrical Controllers with Flipper Zero
Researchers exploit vulnerabilities in the Radio Ripple Control Protocol used to manage critical electrical facilities in several European countries. Demonstrate several remote radio attacks with a Flipper Zero that can shut down electrical controllers.
New Mirai IoT botnet breaks record with 5.6 Tbps DDOS Attack
A variant of the Mirai botnet, primarily composed of vulnerable routers and wireless cameras sets new record for DDOS attack. IoT and networking devices are a persistent and growing security hole.
119 Vulnerabilites in LTE/5G Implementations Disclosed
119 vulnerabilities in major LTE/5G implementations allow attackers to persistently disrupt all cellular communication across cities. Many attacks can be performed from an unauthenticated cellular device without a SIM card. Attackers with access to a home-use femtocell could perform network core breaches, enabling city-wide surveillance of subscriber locations and connections, targeted attacks on specific users, or manipulating core network infrastructure.
Chinese National and Active Duty South Korean Soldier Indicted for Stealing Military Secrets
A Chinese national and an active duty South Korean soldier were indicted for stealing military secrets with a smuggled mobile phone and camera-enabled watch. The theft involved US-South Korean joint exercise documents from the South Korean Military Government on April 25th, 2025.
Hidden Communication Devices in US Solar Grid Infrastructure
In November 2024, solar power inverters in the U.S. and elsewhere were remotely disabled from China. A subsequent investigation over the past 9 months revealed hidden communication devices in Chinese solar power inverters and batteries across the US solar electric grid. The investigation uncovered hidden wireless channels embedded in critical infrastructure and an apparent shutdown of solar inverters during an alleged contract dispute between Chinese solar grid component manufacturers and their distributor. This affected critical industry from November 2024 to May 2025.
2024
Pakistan APT used Hak5 Wireless Pentesting Devices to Infiltrate Indian Gov Buildings
Researchers disclose that a Pakistan Gov linked APT had been using Hak5 devices to communicate large amounts of data from an Indian Ministry of Foreign Affairs office in Europe, an Indian national defense organization, and several other government bodies to a remote Hak5 branded C2 server. Russian APT eventually conmpromised this server for its own cyber operations.
"Hi My Name Is Keyboard" Bluetooth Keystroke Injection Attack
Bluetooth vulnerabilities in modern Android, Linux, macOS, iOS and Windows can be exploited to pair an emulated Bluetooth keyboard and inject keystrokes without user confirmation. No patches are available for older MacOS, iOS, or Android operating systems.
Kali Nethunter Incorporates "Hi My Name Is Keyboard" Automatic Bluetooth Vulnerability Scanning and Ducky Exploit Scripts
Kali Nethunter, a smartphone based wireless pentesting application, expands Bluetooth vulnerability scanning, automates exploitation of Bluetooth pairing vulnerability that leads to 0-click code execution
Kali Nethunter Adds Wi-Fi Pumpkin3 Evil Access Point capabilities
Kali Nethunter adds Wi-Fi Pumpkin3 toolkit, allowing sophisticated evil access point attacks via mobile devices. Now supports over 100 different mobile devices
Novispy Zero-Click Android Spyware Exploiting Several Qualcomm Zero days reported
Serbian government reported to infect phones of activists and reporters with Novispy spyware. Researchers believe the attacks use zero day exploits in the Qualcomm chips that allow device infection via the Android Calling function.
Spyloan Android Malware Infects 8 Million Users
A dozen apps on the Google app store containing hidden Android Spyware are reported to have infected over 8 million users. The malware had continued to evade detection by Google Play.
Joint Cybersecurity Advisory Warns Russian SVR's Exploiting 3 Bluetooth Vulnerabilities
Joint Western Intelligence Agencies issue advisory warning Russian SVR's are exploiting 3 wireless vulnerabilities alongside traditional attacks.
Canada Bans 'Flipper Zero' SDR
Canadian Government bans the Flipper Zero SDR device to combat spate of RF based car-jacking attacks
Cinterion Modem SMS RCE Vulnerabilities
Kaspersky disclosed a severe vulnerability to millions of industrial devices using the cellular Cinterion IoT Modem. Attackers could send malicious SMS messages to these devices to remotely execute arbitrary code and perform unauthorized privelege escalation
Salt Typhoon
Chinese Hackers tap the infrastructure of 9 US Cellular Carriers to listen to calls and steal texts. US Cybersecurity officials warn US citizens to use encrypted communications on mobile devices.
Nearest Neighbor Attack
Russian Hackers use Wi-Fi to break into a network from thousands of miles away
The Russian hacking group, APT 29, puts Zero Click Spyware on watering hole websites.
The Russian-based APT29 group was seen using the same iOS and Google Chrome exploits as commercial surveillanceware vendors NSO Group and Intellexa, in an espionage campaign that targeted the Mongolian government. Researchers do not know how Russian actors gained access to these vulnerabilities.
AI-Powered IoT Attacks
AI-driven malware targets IoT ecosystems, automating the exploitation of weak devices for broader control and surveillance.
NSA Warns All iPhone and Android Users Should Restart Phone Every Week. Turn off Bluetooth.
The National Security Agency (NSA) has recommended that all iPhone and Android users restart their devices at least once a week and to make sure Bluetooth is turned off. The agency states restarting mobile devices can help disrupt the operations of malware and other malicious software that may have infiltrated the system.
Wireless Transmitter Implant in Three-Stars General Name Tag
Chinese spies planted a surveillance chip in a former U.S. three-stars general’s conference name tag to observe him during his time serving in the Indo-Pacific.
2023
US Army Warns of Mysterious Smartwatches Mailed to Servicemembers: Auto-Connecting to Wireless Networks and Devices
Service members across the military have reported receiving smartwatches unsolicited in the mail. These smartwatches, when used, have auto-connected to Wi-Fi and began connecting to cell phones unprompted, gaining access to a myriad of user data.
Flipper DoS Attack on iPhones
A BLE spam attack caused iPhones to freeze and forced them to reboot, creating a wireless denial of service
Triangulation Attack: iPhones infected by malicious iMessage
Kaspersky researchers reported iPhones had been infected with spyware via malicious iMessages that exploited hardware registries in the device that Apple's firmware did not know existed. The device owner would not see they had received a malicious message and the device could be reinfected at any time by receiving another malicious iMessage.
Roaming Mantis Android Malware Spreads via Wirelessly Compromising nearby Wi-Fi routers
The Roaming Mantis campaign was reported to spread its mobile malware to other devices via compromising nearby Wi-Fi routers (e.g., using DNS changers to redirect Android users to malicious servers, distributing Wroba.o malware to steal credentials or hijack devices. Initially targeting South Korean routers, the attack has spread globally as infected devices connect to new networks.
Flying Pineapple
A hedge fund's network was infiltrated after two drones landed on the roof of their building carrying a Wi-Fi Pineapple and other wireless attack equipment
Predator demonstrates Pegasus-like zero click Spyware Capabilities
Predator can intercept communications, activate device sensors, and exfiltrate data. The attack chain shares architectural similarities with other zero-click exploits like Pegasus, but uses chains focused on browser components rather than messaging apps. Predator has recently been reported to have restored its infrastructure and operates in over 11 countries.
5G Vulnerabilities in IoT
Researchers identified weaknesses in 5G protocol implementations, allowing attackers to track and intercept IoT data.
2022
Researchers Discover iPhone can be infected with malware via Bluetooth while powered off
Researchers discover that Low Power Mode for the 'Find My' functionality of the Bluetooth Chip allows UWB, NFC and Bluetooth chips to access the phone's secure element when powered off. They demonstrate that attackers could install malware on the Bluetooth chip that can infect the device while it is powered off.
Pegasus Project exposes 50,000 compromised accounts: journalists, President of France, King of Morocco
The Pegasus Project investigation revealed that NSO Group's Pegasus mobile spyware was used to target at least 14 world leaders, including presidents, prime ministers, and Morocco's king. While some leaders were targeted by rival nations, evidence suggests several countries, including Kazakhstan, Mexico, and Morocco, conducted surveillance on their own officials.
FragAttacks on Wi-Fi
Fragmentation and Aggregation Attacks (FragAttacks) expose vulnerabilities in Wi-Fi implementations, affecting devices from multiple vendors.
2021
BlueJacking: A hijacking attack against Bluetooth-enabled devices
Bluejacking is a form of wireless exploitation that takes advantage of Bluetooth technology's device discovery capabilities. The attack occurs when a malicious actor sends unsolicited messages or files to nearby Bluetooth-enabled devices that have their visibility set to "discoverable." The vulnerability exists due to Bluetooth's inherent device pairing process and limited range security controls.
BrakTooth exposes billiions of devices to Bluetooth vulnerabilities
Researchers discover “BrakTooth,” a series of vulnerabilities in 13 manufacturer's SoC chip Bluetooth stacks that allow attackers to execute code, crash devices, or disrupt connections. The vulnerabilities affected billions of devices across critical industry, IoT, Automobile manufacturing, and consumer electronics. Several manufacturers announced they would not release patches, or would only patch vulnerable devices on request.
LTE Layer Attacks
Researchers discovered that attackers could exploit vulnerabilities in LTE networks to track devices and intercept calls or data.
IoT Ransomware Emerges
Hackers began targeting IoT devices like smart thermostats and cameras with ransomware attacks.
2020
Zigator Toolkit Released
This Zigbee attack suite includes functions for impersonating devices, disconnecting devices, leaking credentials, conducting reconnaissance, MitM attacks, and more
Phillips Hue Smart Bulbs Allow Network Compromise Over Zigbee Vulnerability
Researchers discovered a vulnerability (CVE-2020-6007) in Philips Hue smart bulbs that allows hackers to infiltrate networks through installing malware on the device through the ZigBee protocol. The malware then connects back to the hacker, who can use known exploits and vulnerabilities to enable IP network infiltration and malware propagation
BlueSmacking: A denial of service attack against Bluetooth-enabled devices
BlueSmacking is a denial-of-service attack against devices that exploits the L2CAP protocol ping mechanism. Attackers can overwhelm targeted device's resources by sending oversized ping packets via Bluetooth and potentially cause system crashes. The Kali Nethunter app allows certain android phones to conduct these attacks on any nearby Bluetooth devices.
Sweynetooth
The SweynTooth vulnerability family consists of 12 BLE vulnerabilities affecting multiple IoT device manufacturers. These flaws allow attackers within radio range to cause device crashes, deadlocks, and security bypasses. Millions of devices are vulnerable to these attacks, including smart home devices, fitbits, and medical devices.
Bluetooth BlueFrag Android Vulnerability
A critical Bluetooth vulnerability (CVE-2020-0022) affected Android 8.0-9.0 devices, allowing remote code execution without user interaction when Bluetooth was enabled. Android 10 was partially affected.
Ripple20 Vulnerabilities
Discovered in the Treck TCP/IP stack used by IoT devices, Ripple20 allowed remote code execution on millions of devices.
IoT Worm Attacks
Botnets like Mozi targeted IoT devices with weak security to spread malware and launch DDoS attacks.
2019
Large scale SS7 Attacks on Mobile Banking Users
Bank acccounts around the world are reported to be hacked by cybercriminal groups using SS7 vulnerabilities to intercept 2-factor authentication codes.
O.MG Cable
The O.MG Cable is a pentesting device that appears identical to a standard charging/data cable but contains a malicious implant allowing remote automated keystroke and payload injection via an embedded wi-fi antenna in the cable.
Wi-Fi Dragonblood
Vulnerabilities in WPA3 are discovered, dubbed “Dragonblood,” exposing flaws in the new Wi-Fi security standard. The vulnerabilities affected billions of Wi-Fi enabled devices, and allowed attackers to downgrade connections, perform side-channel attacks, and potentially extract network passwords.
BLE Spoofing
Researchers demonstrated spoofing attacks on Bluetooth Low Energy (BLE) devices, compromising secure connections and allowing attackers to inject spoofed data into the device. The vulnerabilities were reported to affect up to one billion Linux, Android, and iOS devices, worldwide
Trend Micro Identifies Severe RF Vulnerabilities in ICS Equipment
The research identified several attack vectors that can be executed within 300 meters range (or several kilometers with signal amplifiers). Affected devices include tower cranes, industrial cranes, and mobile hoists.
2018
Department of Homeland Security Identifies Rogue IMEI Catchers in DC
DHS says it has observed "anomalous activity" consistent with Stingrays in the Washington area.
GRU Agents Conduct Wi-Fi Attacks in Netherlands
Four GRU agents were apprehended after conducting Wi-Fi attacks in the Netherlands
BTLEJack Toolkit Released
Bluetooth attack suite for sniffing, jamming, and/or hijacking BLE networks
Jeff Bezos' cell phone gets hacked
In 2018, Jeff Bezos's phone was hacked after receiving a malicious video via WhatsApp from Saudi Crown Prince Mohammed bin Salman. The video exploited a zero-day vulnerability, installing spyware that extracted sensitive data. The attack was linked to Saudi retaliation over The Washington Post’s critical reporting. Forensic analysis pointed to state-sponsored hacking, highlighting risks to high-profile individuals.
NASA JPL Wireless Implant Hack
A cybersecurity audit revealed that an attacker had managed to wirelessly exfiltrate data out of NASA's Jet Propulsion Laboratory, undetected for over 10 months. The attacker used a raspberry pi they had connected directly to network infrastructure at the laboratory which they remotely controlled via a wireless conection to the device.
SirenJack
Bastille discovered SirenJack, a vulnerability in ATI Systems' emergency sirens, allowing remote activation via unencrypted radio signals, risking false alarms and public panic.
Dark Vishnya Malicious Wireless Implant Attack on European Banks
Kaspersky reports a series of 8 seperate attacks on European banks where attackers used malicious hardware implants that they direclty connected to bank networking routers. The devices had embedded cellular modems which attackers used to remotely access the implants and eventually infiltrate the bank's inner network. Estimated losses are $8 million
Bluetooth KNOB Attack
Key Negotiation of Bluetooth (KNOB) attack is revealed, exploiting weaknesses in Bluetooth’s key negotiation process to intercept encrypted communication. The KNOB attacks affected Bluetooth chips from 17 different manufacturers, impacting over a billion devices worldwide.
LTE Protocol Exploits
Researchers identified flaws in LTE protocols, enabling impersonation attacks, eavesdropping, and tracking.
Amazon Echo and Alexa Exploited
Security researchers used ultrasonic waves to exploit IoT voice assistants, forcing them to execute unauthorized commands.
2017
BlueBorne Bluetooth Vulnerability
Researchers identified a series of vulnerabilities potentially affecting an estimated 5.3 billion Bluetooth devices that allow attackers to compromise devices without Bluetooth pairing or approval. The Researchers created a botnet of infected devices using the BlueBorne attack vector as a worm to infect other nearby Bluetooth devices.
KRACK Attack on WPA2
The Key Reinstallation Attack (KRACK) exploits vulnerabilities in WPA2 protocol, allowing attackers to intercept, decrypt and manipulate Wi-Fi traffic.
2016
MouseJack
Bastille discovers MouseJack family of vulnerabilities affecting wireless non-Bluetooth peripherals, enabling attackers to inject keystrokes via radio signals from 100 meters away, exploiting unencrypted mouse and keyboard data to bypass security.
KeyJack
Bastille discovers the KeyJack vulnerability, allowing attackers to send encrypted keystrokes to be injected into a vulnerable wireless keyboard’s dongle without knowledge of the encryption key.
Mirai Botnet
Mirai exploited weak or default passwords in IoT devices, forming a massive botnet used in DDoS attacks.
2015
Chrysler Jeep Hack
Hackers remotely controlled a Jeep Cherokee over its cellular connection, demonstrating the vulnerabilities of connected cars.
2014
Ebay sells cheap RF Video Bugs
Video and audio spying devices with embedded remote wireless communication become widely available on online marketplaces.
Bastille Networks Founded
Former ISS security experts, SDR specialists from Georgia Tech, and alumni of the DARPA Spectrum Challenge joined forces to establish Bastille Networks in Atlanta, Georgia.
Heartbleed Vulnerability
This OpenSSL bug impacted many IoT devices, exposing sensitive data in wireless communications.
SS7 Telecom Network MiTM Vulnerability Disclosed
Vulnerabilities to the SS7 telecomunications protocol allow attackers to conduct Man-in-The-Middle attacks to intercept and eavesdrop on individual's mobile communications and track their location. These attacks continue to be reported today.
2013
Bluetooth PIN Brute Force
Researchers demonstrated brute-force attacks against Bluetooth pairing, exposing weaknesses in PIN-based pairing mechanisms.
2012
Mexico Pays $20MM for Pegasus Subscription
The Mexican Government purchases license for Mobile Zero-Click Spyware, Pegasus. It eventually becomes largest reported user of the software.
2011
NSO starts to build Cell Phone Spyware
Israeli based NSO Group completes development of sophisticated, zero-click spyware, Pegasus. Begins selling licenses for use to Governments.
Wi-Fi WPA2 Vulnerabilities
Researchers demonstrate flaws in WPA2 networks, including weak password implementations.
LTE IMSI Catchers Introduced
Rogue LTE base stations (IMSI catchers or Stingrays) were used to intercept mobile communications and track users.
2010
Advanced SDR based RF Hacking Tools released
The development of Software-Defined Radio (SDR) allowed for more versatile and powerful RF hacking capabilities. Tools like the HackRF One enabled researchers and hackers to analyze and exploit a wide range of RF signals, from satellite communications to keyless entry systems.
Bluetooth BlueBugging
“BlueBugging” becomes a recognized threat, allowing attackers to gain control of devices via Bluetooth to make calls or send messages.
Stuxnet Malware
Stuxnet exploited vulnerabilities in industrial control systems, including wireless IoT protocols, to sabotage Iran’s nuclear facilities.
2008
Wi-Fi Evil Twin Attacks
“Evil Twin” attacks gain traction, where attackers set up rogue access points to mimic legitimate networks and intercept user data.
Hak5 pineapple
The Wi-Fi Pineapple is released as a simple to use, pre-configured Evil Twin Attack platform, sold for pentesting.
RFID Cloning Exploits
Researchers successfully cloned RFID tags, compromising security systems reliant on this technology.
ATM Wireless Hardware Supply Chain Compromise
Credit card readers used in UK supermarkets had a wireless device inserted in them by the manufacturer in China. The device copied a credit card when inserted, and transfered the information via a Wi-Fi connection to Lahore, Pakistan. Estimated losses were $50 million.
BeSeLo: Bluetooth + MMS Worm
Researchers discovered a new Bluetooth and MMS worm attacking mobile phones running on the S60 software platform. Similar to CommWarrior, the worm spread via MMS and then to any nearby devices within Bluetooth range.
ZigBee Vulnerabilities
ZigBee, a popular protocol for IoT devices, was found to have weak key management, enabling attackers to hijack IoT devices.
2005
Bluetooth BlueSnarfing
“BlueSnarfing” is discovered, where attackers can exploit Bluetooth to steal data from nearby devices without user consent.
CommWarrior: Bluetooth + MMS Worm
The CommWarrior worm exploited MMS and Bluetooth vulnerabilities in mobile devices running on the Nokia S60 platform to spread and steal information from the device. Over 100,000 devices were discovered to be infected by CommWarrior.
2004
Cabir Bluetooth Attack: 1st Mobile Device Worm
Kaspersky researchers reported on the first worm affecting mobile devices. Cabir would attempt to infect all nearby Bluetooth devices that accepted the Object Push Profile, which included SymbOS mobile devices, some laptops, and some printers.
2003
WAP1 vulnerabilities exposed
2001
Maroochy Shire Wastewater SCADA Radio Attack
A disgruntled SCADA engineer issued over 2,000 radio commands to radio controlled pumping stations around Maroochy Shire, Australia. Over the course of several months he released over 1,000,000 gallons of raw sewage throughout the area. The engineer was caught with radio equipment in his truck that he had been using to remotely control the pumps.
First WEP Cracks
Researchers demonstrate how WEP can be cracked in under 2 hours using freely available tools like AirSnort or WEPCrack, marking one of the earliest major Wi-Fi security breaches.
2000
Bluetooth and RFID Vulnerabilities
The widespread adoption of Bluetooth and RFID technologies introduced new attack vectors. Hackers demonstrated the ability to exploit vulnerabilities in these wireless protocols to gain unauthorized access to devices and data.
1999
WEP Introduced
Wired Equivalent Privacy (WEP) is introduced to secure Wi-Fi. Soon after, vulnerabilities are discovered due to weak encryption (RC4 key reuse issues).
1997
The Birth of Wi-Fi
IEEE releases the 802.11 standard, the first official Wi-Fi specification. Security concerns are minimal at this stage.
1991
First GSM Networks Launched
Vulnerabilities in the GSM encryption algorithm (A5/1) were later exploited, allowing attackers to intercept and decrypt GSM communications.
1990
Wireless Network Exploitation
As wireless networks became more prevalent, hackers began exploiting weaknesses in Wi-Fi security protocols. Tools were developed to intercept and decrypt wireless communications, leading to increased awareness of the need for robust wireless security measures.
IEEE begins development of the 802.11 standard
IEEE begins development of the 802.11 standard, which would eventually become Wi-Fi.
1985
FCC Opens ISM bands for unlicensed use
The U.S. FCC opens ISM bands for unlicensed use, enabling the future of wireless communication standards like Bluetooth and Wi-Fi.
1980
1980s Computer and Wireless Hacking Emergence
The rise of personal computers led to the emergence of computer hacking. In 1988, the Morris Worm became one of the first widely recognized computer worms, disrupting numerous systems and highlighting vulnerabilities in network security.
1970
Phone Phreaking
Individuals known as "phone phreaks" exploited the telephone system to make free calls and explore the network. They used devices like the "blue box" to manipulate phone systems, representing an early form of hacking into communication networks.
1950-1960's
1950s-1960s: Cold War Espionage
During this period, both Western and Eastern bloc intelligence agencies developed advanced listening devices, including covert bugs and wiretaps, to gather information. These devices became more sophisticated, utilizing miniaturization and improved transmission techniques.
1945
The Thing
In 1945, Soviet inventor Leon Theremin designed "The Thing," a passive listening device hidden inside a replica of the Great Seal of the United States. Presented to the U.S. Ambassador in Moscow, it allowed eavesdropping without any active power source, marking a significant advancement in espionage technology.
1903
The Marconi hack
The origins of wireless and RF hacking date back to June 4, 1903, in London, during Marconi's demonstration of his wireless system, which he claimed could securely transmit messages over long distances without wires. However, the presentation was sabotaged when an intruder intercepted the signal, publicly mocking him with Morse code. This incident revealed critical vulnerabilities in his technology, challenging claims of secure wireless communication.
Request a Demo
See how the most advanced wireless airspace cybersecurity solution provides 24/7 visibility and protection for your critical infrastructure.
