Wireless intrusion detection systems (WIDS) identify and mitigate attempts to gain unauthorized access to data or intel in government and corporate spaces. While they succeed at finding threats within the traditional network perimeter, they miss many other signals that may indicate risky or malicious behavior. Modern WIDS are part of a larger solution that can stay ahead of the evolving wireless threat landscape.
What is a wireless intrusion detection system (WIDS) ?
Wireless intrusion detection systems (WIDS) are designed to monitor wireless networks for unauthorized access and potential intrusions by scanning for wireless threats and alerting security teams when one is detected. Because WIDS are traditionally more network-focused and have trouble identifying low-energy and clandestine devices, these solutions are not comprehensive and must be paired with technology that can provide additional breadth and business context to the organization’s threat data.
Capabilities of Wireless Intrusion Detection Systems (WIDS)
Wireless Intrusion Detection Systems (WIDS) monitor and analyze radio frequency signals across Wi-Fi and other wireless networks to detect unauthorized access points, rogue devices, suspicious transmissions, and policy violations in real-time. They provide continuous surveillance, alert administrators to potential threats.
Spectrum Monitoring: Continuously scans wireless frequencies to detect signals, interference, and unauthorized transmissions.
Device Fingerprinting: Identifies and classifies devices by their unique radio and network characteristics.
Threat Detection & Alerting: Detects suspicious activity and unauthorized devices, providing immediate alerts to administrators.
Device Localization: Pinpoints the physical location of wireless devices within the monitored area.
Historical Analysis: Stores and reviews past wireless activity for forensic investigation and compliance reporting.
WIDS is now required in the Department of Defense
Following high profile SCIF data exfiltration, the Secretary of Defense (SECDEF) initiated a DoD wide review of SCIF and SAPF security. The resulting SECDEF memo on June 30th, 2023 requires Department of Defense Services and Agencies to program and implement appropriate electronic device detection systems and mitigation measures to ensure the integrity of National Security and Mission needs, protecting against US National Security data exfiltration. (Full SECDEF memo available here)
“Electronic device detection shall be continuous, comprehensively covering the entirety of Department SCIF and SAPFs, with immediate identification, precise device location, and alerting to the appropriate facility personnel, with full audit and time series data, providing a device’s pattern of life over time and space. Uninterrupted SCIF and SAPF observation telemetry data shall provide device type, location, and historic accounting of the device’s presence within the SCIF and SAPF, with data provided to the appropriate security and insider threat teams, as necessary. Electronic device detection systems shall protect the integrity of the SCIF and SAPF spaces with a permanently installed observation system.
Systems shall provide complete observability of the entirety of the SCIF and SAPFs spaces. Programming efforts shall include the cost of the electronic device detection system, system installation costs and planned out-year sustainment costs.”
The SECDEF memo follows several Federal policies and instructions, such as DoDI 8420.01 require that agencies secure and protect their Wireless infrastructure, where the WIDS solution:
“must continuously scan for and detect authorized and unauthorized WLAN activities 24 hours a day, 7 days a week. Scanning must include a location-sensing capability that enables designated personnel to locate, identify, and take appropriate actions to mitigate…” DoDI 8420.01 Section 3.
As WIDS solution requirements have evolved, where once it was sufficient to locate and identify Wi-Fi devices, at a minimum a solution must now accurately detect and locate Bluetooth, Bluetooth Low Energy and devices only emitting cellular signals.
For clarity, this means a comprehensive cell phone detection and location product must be able to discover a cell phone even when the Wi-Fi and Bluetooth are not active.
The limitations of traditional WIDS
THEY CAN’T DISTINGUISH BETWEEN MULTIPLE DEVICES
Legacy WIDS based on spectrum analyzers simply alert security teams when they detect energy in a cellular frequency. These products cannot distinguish between one phone close to a sensor or 10 phones farther away. Without this knowledge, there’s no way to know which devices to look for and where, or the exact nature of each threat.
THEY DON’T SEE EVERYTHING BEYOND THE NETWORK PERIMETER
Standalone WIDS solutions miss a large portion of wireless threats, including devices that are disabled or not on known networks. They also have trouble detecting low-energy devices and non-agentable wearables like building access badges.
THEY CAN’T PINPOINT AN ACCURATE, REAL-TIME LOCATION FOR EACH DEVICE
Distinguishing and locating individual cell phones, and placing an accurate dot on a map to pinpoint exactly where a cell phone is at a given moment, is a very hard problem. While WIDS solutions are capable of confirming a threat’s presence in a space, they can’t track location or playback historical movement.
What does a modern wireless intrusion detection system (WIDS) do?
A modern WIDS is typically part of a larger Wireless Airspace Cybersecurity solution and can detect a broader range of threats. Bastille incorporates WIDS capabilities into a comprehensive platform that removes classic limitations and provides real-time data on every wireless device, network, and threat in your space.
ACCURATELY LOCATE CELL PHONES INSIDE YOUR FACILITY USING JUST THIER CELLULAR SIGNALS
Many WIDS solutions claim to detect smartphones, but in reality only detect Bluetooth and Wi-Fi signals (rather than cellular signals) or the presence of cellular energy. As a result, these systems cannot differentiate between one phone close to a sensor and 10 phones farther away. Today, a WIDs solution must go beyond basic Bluetooth and Wi-Fi tracking to include hard-to-detect low-energy signals and burner phones.
CONTINUOUS CELL PHONE AND ACTIVITY MONITORING
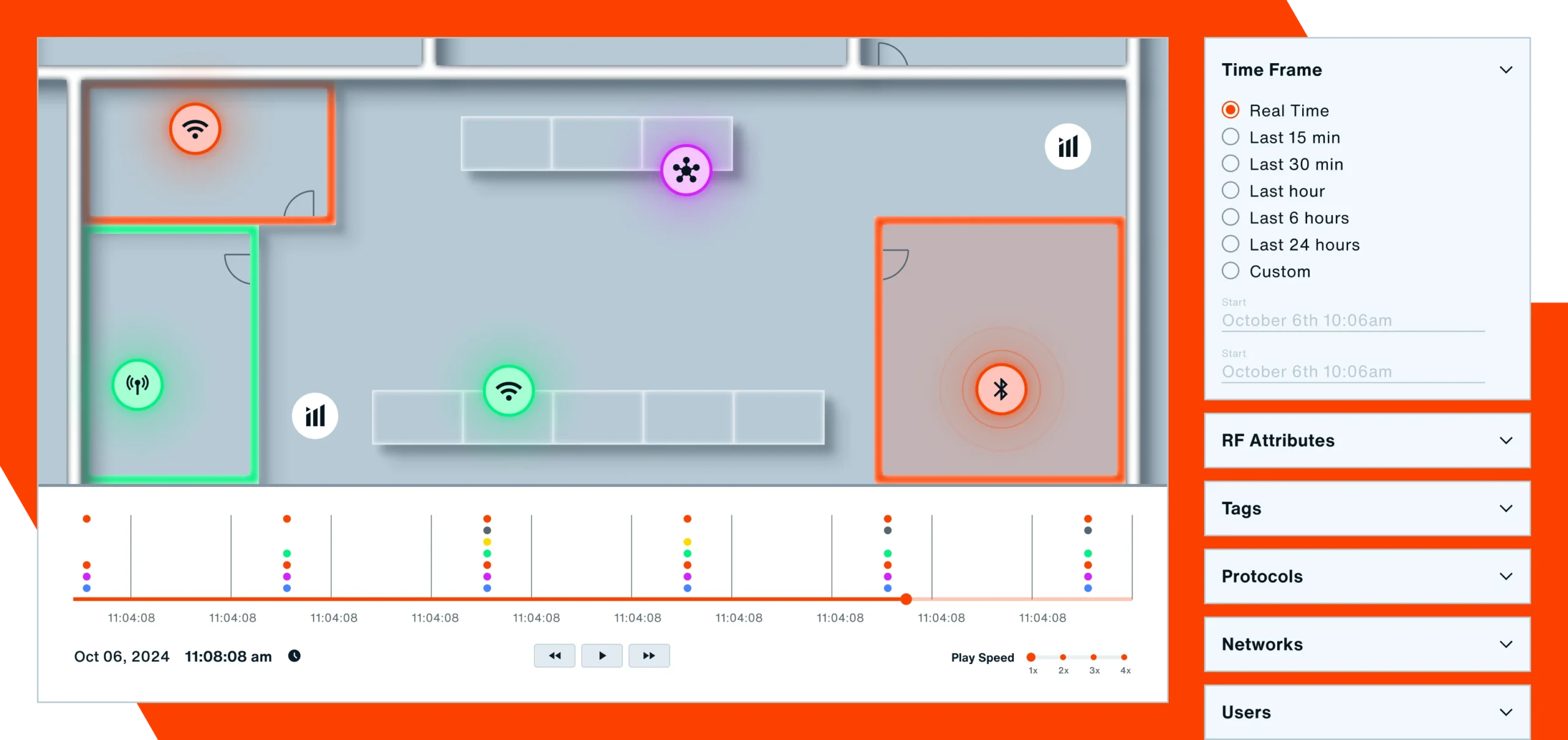
A modern WIDS continuously monitors your facilities for the presence of cell phones. Bastille tracks the location of every cell phone and wireless device as it moves through your building, updating location data in your wireless asset inventory.
These systems should also alert you of relevant or suspicious activity. If someone brings a cell phone into the building which is powered down, for example, Bastille can alert you when it is powered back up in your facility. The platform will also alert you when the device enters a restricted area.
ADVANCED THREAT DETECTION ACROSS ALL CHANNELS SIMULTANEOUSLY
Bastille’s sensor arrays provide advanced detection and location for Wi-Fi and bluetooth. For example, Bastille is constantly demodulating all 79 bluetooth channels all the time. This is in contrast to other technologies that only listen to one Bluetooth channel at a time. That is, other devices can only see 1.2% of the traffic that Bastille can see. Moreover, by listening to all channels, all of the time, Bastille’s patented device and traffic fingerprinting machine learning technology can determine the types of data traffic being conveyed by each Bluetooth network. For example, Bastille can tell the difference between malicious Bluetooth tethering events and other innocuous events like music streaming.
Some organizations allow employees to bring personal cell phones into secure facilities but ask them to leave the secure area if a call comes in. Bastille alerts you when an inactive personal cell phone becomes active and lets you track whether it leaves the secure area to continue to call.
DETECT BOTH ENDS OF BLUETOOTH PAIRING
Many locations approve and permit certain Bluetooth or BLE devices within their secure facilities, like medical devices such as hearing aids or insulin pumps. However, when even an approved BT/BLE device pairs with another device, that typically contravenes the policy to permit that device, as there is a live connection which can exfiltrate data, voice, or video. Bastille is the only solution which can detect both ends of a Bluetooth pairing and alert upon it.
DETECT AND ALERT IN REAL TIME VIA INTEGRATIONS
Bastille alerts on the presence of a cellular phone in a facility within two seconds and alerts through the system of your choice via open standards based APIs.
Bastille integrates with your existing SIEM and/or alerting systems via its open standards based APIs. Native Integration with systems like Splunk(R) and Elasticsearch/Kibana(R), PagerDuty(R), SMS and email. Alternatively customers can view alerts via the Bastille GUI, and use that platform to dig into alerts for more information.
LOCATE WIRELESS DEVICES AND THREATS DOWN TO 1-3 METERS
Bastille sees every cellular phone within a space and puts a separate dot on the map to mark the location of each device. Location accuracy is 1 to 3 meters.
DETAILED HISTORY OF CELL PHONE LOCATION AND ACTIVITY IN YOUR FACILITIES
In addition to showing you where cell phones are right now, Bastille’s DVR functionality lets you look back over days or weeks and see where cell phones in your building were 3 weeks ago and how they moved around your facility. This forensic capability contributes to security investigations.
Bastille records all the cell phones seen, and their movements, to permit DVR-like playback for forensic purposes. If you want to find out what happened in your facility 2 months ago, simply jump back to that date and replay all activity before and after that event.
100% PASSIVE, FULLY COMPLIANT SENSING TECHNOLOGY
Bastille was originally designed for use in the Enterprise where there are no special exceptions from FCC regulations as exist for certain Federal Government users. Consequently Bastille is a 100% passive technology and complies with all FCC requirements and is currently approved for use in Government and Corporate environments.
Bastille provides a passive monitoring solution by allowing firms to detect and locate cellular phones without accessing data content, thus alleviating key privacy concerns.
CUSTOMIZABLE GEO-FENCES AND POLICIES
Bastille’s ability to accurately detect and locate cell phones, and distinguish between multiple phones leads to the ability to create a geo-fenced area within a facility, set a policy for that area, and alert when a phone enters. For example, the trading floor or research lab can be “geo-fenced” and alerts sent when an unauthorized cell phone enters.
What type of threats can WIDS detect and alert on?
Today’s most advanced solutions can detect a number of wireless devices and threats that are especially dangerous for government entities and highly regulated industries.
CELLULAR INTRUSION
Most companies only track signals like Bluetooth and Wi-Fi, even when bad actors attempt to turn off those signals. Bastille’s Cellular Intrusion Detection is the first system which accurately detects, counts, and locates cellular devices inside your facility in real-time, 24×7. This capability is critical to fully locking down your facility from unauthorized devices.
UNAPPROVED OR UNMANAGED DEVICES AND NETWORKS
Bastille’s WIDS capabilities pinpoint threats from devices that are not controlled by an MDM or XDR and may not be authorized to operate in the facility. By going beyond the network perimeter to identify personal devices, wearables, and IoT that aren’t explicitly allowed, the platform gives you more coverage than any traditional WIDS.
INSIDER THREATS AND NON-COMPLIANT USAGE
With the ability to accurately detect cell phones, enterprises and government agencies will finally have a solution to a serious set of problems which until now have only been solved using the “Honor System”. Under the Honor System employees, contractors, and visitors are asked to leave their cell phones outside an area or not use them within an area. This system too often fails due to an oversight from a well-intentioned actor or a malicious action from a bad actor.
FAQs About Wireless Intrusion Detection Systems (WIDS)
What is a Wireless Intrusion Detection System (WIDS)?
A WIDS is a system that monitors wireless signals like Wi-Fi, Bluetooth, and cellular for unauthorized access or suspicious behavior. It alerts security teams in real-time, helping protect sensitive facilities from wireless-based threats.
What types of threats can WIDS detect?
Bastille’s WIDS can detect unauthorized devices, cellular intrusions, rogue networks, insider threats, low-energy wearables, and Bluetooth pairings that may violate policy or signal data exfiltration attempts.
Is WIDS required for government agencies like the DoD?
Yes. Following security incidents, the Department of Defense now mandates 24/7 wireless device detection in SCIFs and SAPFs. Bastille meets and exceeds these federal requirements with continuous coverage and precise threat detection.
What is the difference between WIPS and WIDS?
WIDS passively detects wireless threats and alerts security teams. WIPS (Wireless Intrusion Prevention System) takes it further by actively blocking or disconnecting unauthorized devices. WIDS watches; WIPS watches and acts.
What are the disadvantages of WIDS?
Traditional WIDS may struggle with pinpointing device locations, detecting low-energy or passive threats, and distinguishing between multiple nearby signals. They can also lack integration with broader security infrastructure unless modernized.
How does one implement a wireless intrusion detection system?
Start by identifying high-security areas and risk zones. Deploy passive sensors, like Bastille’s, throughout the facility to monitor all wireless activity. Integrate the system with your existing security stack to centralize alerts and insights.
Is Bastille’s WIDS compliant with privacy regulations?
Yes. Bastille is 100% passive and FCC-compliant. It does not intercept or decode content, it only detects the presence and location of devices, making it suitable for both government and corporate use.
Can WIDS detect wearables and low-energy devices?
Yes. While traditional WIDS only focuses on Wi-Fi, Bastille’s WIDS detects more than just phones and laptops. It detects and locates low-energy devices, such as wearables, wireless earbuds, Bluetooth-enabled medical devices, IoT devices, and other wireless emitters, which traditional WIDS tools often miss.
How does WIDS help detect insider threats?
Traditional WIDS detects unauthorized wireless networking activity. Bastille’s WIDS identifies and locates all wireless personal devices entering secure areas. It provides real-time alerts and records device movements, giving security teams a clear view of non-compliant behavior or potential insider threats.