
In today’s interconnected world, wireless technology is an integral part of corporate infrastructure. As businesses continue to rely on wireless networks for daily operations, the importance of securing these networks has never been more critical.
Employees and visitors bring wireless devices into corporate facilities. Visiting wireless devices may be unwittingly compromised or used by bad actors to compromise corporate assets and networks, exfiltrating voice and data or introducing threats and vulnerabilities to corporate systems.
This is where Wireless Threat Intelligence (WTI) comes into play. WTI provides organizations with the tools and insights needed to detect, analyze, and mitigate threats to their wireless environments. In this article, we will explore the significance of Wireless Threat Intelligence and its impact on modern corporate security.
Understanding Wireless Threat Intelligence
Wireless Threat Intelligence refers to the collection, analysis, and dissemination of information regarding threats to wireless networks. This encompasses a range of activities, including the identification of unauthorized access points, detection of anomalous network behavior, rogue wireless devices and networks, and analysis of wireless vulnerabilities. By leveraging WTI, organizations gain a comprehensive understanding of the threats facing their wireless environments and take proactive measures to safeguard their networks.
The Evolution of Wireless Threats
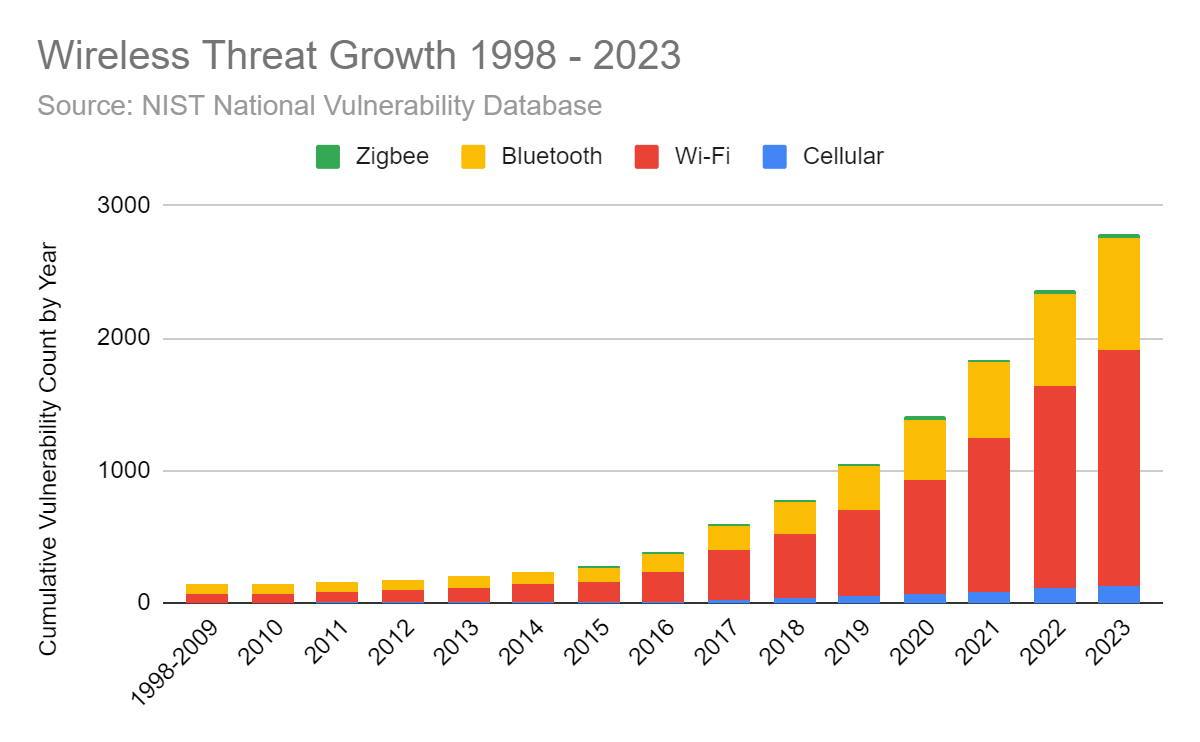
Wireless threats have evolved significantly. Initially, the primary concern was securing Wi-Fi networks from unauthorized access. However, with the advent of advanced technologies and sophisticated attack techniques, the threat landscape has become increasingly complex. Today, organizations must contend with a wide array of wireless threats, using Wi-Fi, cellular and IoT protocols including:
Rogue Access Points: Unauthorized devices that mimic legitimate access points to intercept sensitive information.
Man-in-the-Middle (MitM) Attacks: Intercepting and altering communication between two parties without their knowledge.
Wireless Eavesdropping: Unauthorized listening to private communications over wireless networks.
Denial of Service (DoS) Attacks: Disrupting wireless services by overwhelming the network with traffic.
Bluetooth Exploits: Attacks that target Bluetooth connections to gain unauthorized access or spread malware.
These evolving threats underscore the need for Wireless Threat Intelligence to detect and mitigate potential risks effectively.
The Importance of Wireless Threat Intelligence in Corporate Security
Wireless Threat Intelligence is crucial for several reasons:
Proactive Threat Detection
One of the primary benefits of WTI is its ability to detect threats proactively. Traditional security measures often rely on reactive approaches, addressing threats only after they are identified. In contrast, WTI enables organizations to identify potential threats before they cause significant damage. By continuously monitoring wireless networks and the airwaves for suspicious activity, WTI will alert security teams to potential risks in real-time, allowing for swift and effective response.
Enhanced Visibility and Control
Wireless Threat Intelligence provides organizations with enhanced visibility into their wireless environments. This includes identifying all devices connected to the network, monitoring their behavior, and detecting any anomalies that may indicate a security breach. With this level of visibility, organizations maintain greater control over their wireless networks, ensuring that only authorized devices have access and that any suspicious activity is promptly addressed. In addition, WTI finds wireless devices that are in the facility but are not connected to the network, including cellular devices and those that use IoT protocols.
Improved Incident Response
In the event of a security breach, WTI plays a critical role in incident response. By providing detailed information about the nature of the threat and the affected systems, WTI enables security teams to respond quickly and effectively. This includes isolating compromised devices, mitigating the impact of the attack, and preventing future incidents. With Wireless Threat Intelligence, organizations minimize the damage caused by security breaches and ensure a swift recovery.
Compliance and Regulatory Requirements
Many industries are subject to strict regulatory requirements regarding the security of their wireless networks. Compliance with these regulations often necessitates the implementation of advanced security measures, including Wireless Threat Intelligence. By leveraging WTI, organizations ensure that they meet regulatory requirements and avoid potential penalties. This is particularly important in industries such as healthcare, finance, and government, where the security of sensitive information is paramount.
Implementing Wireless Threat Intelligence
Implementing Wireless Threat Intelligence requires a multi-faceted approach that encompasses several key components:
Wireless Intrusion Detection Systems (WIDS)
Wireless Intrusion Detection Systems (WIDS) are a critical component of WTI. These systems monitor wireless networks and wireless devices for suspicious activity, then alert security teams to potential threats. WIDS detects a wide range of threats, including rogue access points, unauthorized devices, and anomalous network behavior. By integrating WIDS into their security infrastructure, organizations enhance their ability to detect and respond to wireless threats.
Machine Learning and AI
Machine learning and artificial intelligence (AI) play an increasingly important role in Wireless Threat Intelligence. These technologies enable organizations to analyze vast amounts of data and identify patterns that may indicate a security threat. By leveraging machine learning and AI, organizations enhance their ability to detect and respond to wireless threats in real-time.
Employee Training and Awareness
Employee training and awareness are critical components of an effective WTI strategy. Organizations must ensure that their employees are aware of the risks associated with wireless networks and are trained to recognize potential threats. This includes educating employees about safe wireless practices, such as avoiding public Wi-Fi networks and recognizing phishing attempts. By fostering a culture of security awareness, organizations reduce the risk of wireless threats.
Continuous Monitoring and Updates
Wireless Threat Intelligence is not a one-time effort but an ongoing process. Continuous monitoring and regular updates are essential to keep up with the evolving threat landscape. Organizations must invest in technologies and practices that allow for constant vigilance and adaptation to new threats. This includes updating threat intelligence databases, refining detection algorithms, and ensuring that security policies remain current and effective.
The Future of Wireless Threat Intelligence
As wireless technology continues to evolve, so too will the threats facing corporate networks. Emerging technologies such as 5G and the Internet of Things (IoT) present new opportunities and challenges for Wireless Threat Intelligence. To stay ahead of these evolving threats, organizations must continue to invest in advanced WTI solutions and stay informed about the latest developments in wireless security.
The Impact of 5G on Wireless Threat Intelligence
The rollout of 5G technology promises faster speeds and more reliable connections. However, it also introduces new security challenges. The increased bandwidth and connectivity offered by 5G can be exploited by cybercriminals. Organizations must adapt their Wireless Threat Intelligence strategies to address the unique risks associated with 5G networks.
Securing the Internet of Things (IoT)
The proliferation of IoT devices adds another layer of complexity to wireless security. Each connected device represents a potential entry point for cyber threats. Effective Wireless Threat Intelligence must include strategies for securing IoT devices, such as implementing authentication mechanisms, ensuring firmware updates, and monitoring for anomalous behavior.
Conclusion
In conclusion, Wireless Threat Intelligence is a critical component of modern corporate security. By providing organizations with the tools and insights needed to detect, analyze, and mitigate wireless threats, WTI enables businesses to protect their networks and ensure the security of their sensitive information. As the threat landscape continues to evolve, the importance of Wireless Threat Intelligence will only continue to grow. Organizations that invest in advanced WTI solutions and adopt a proactive approach to wireless security will be better equipped to navigate the challenges of the digital age and safeguard their operations against emerging threats.



