Secure the unseen with a wireless airspace defense platform
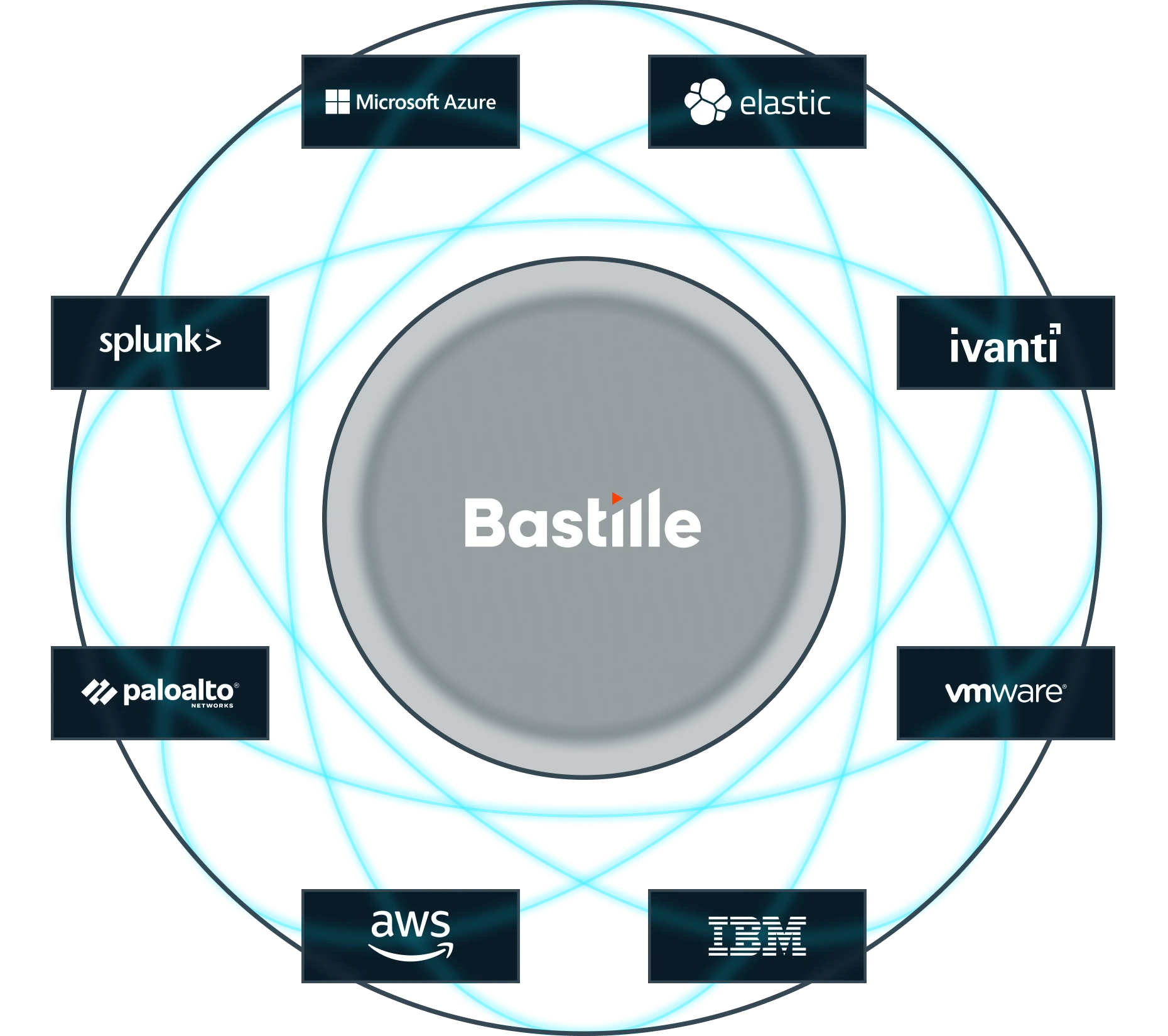
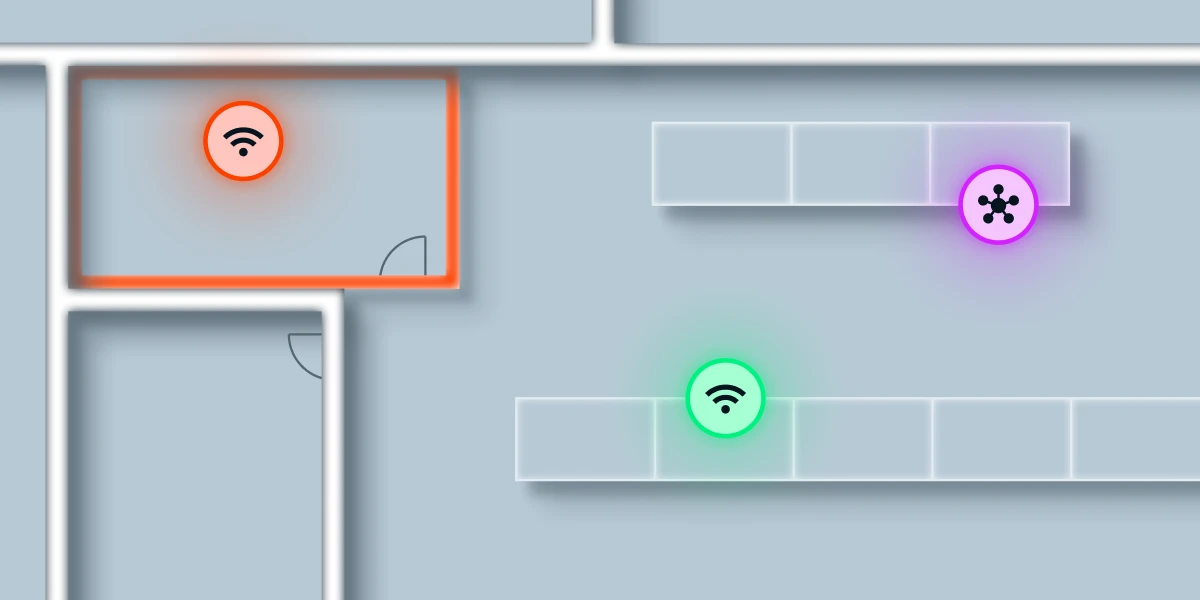
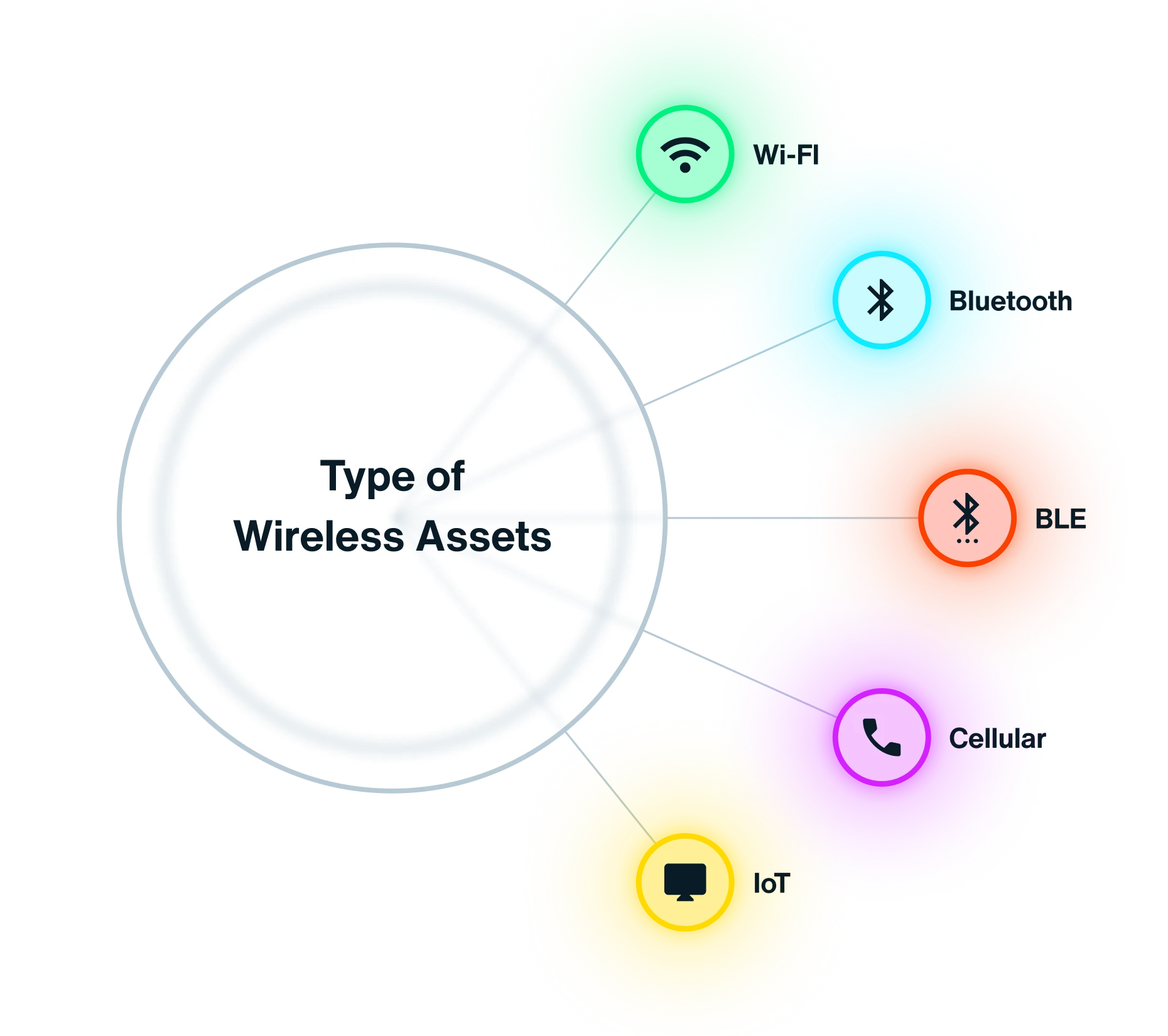
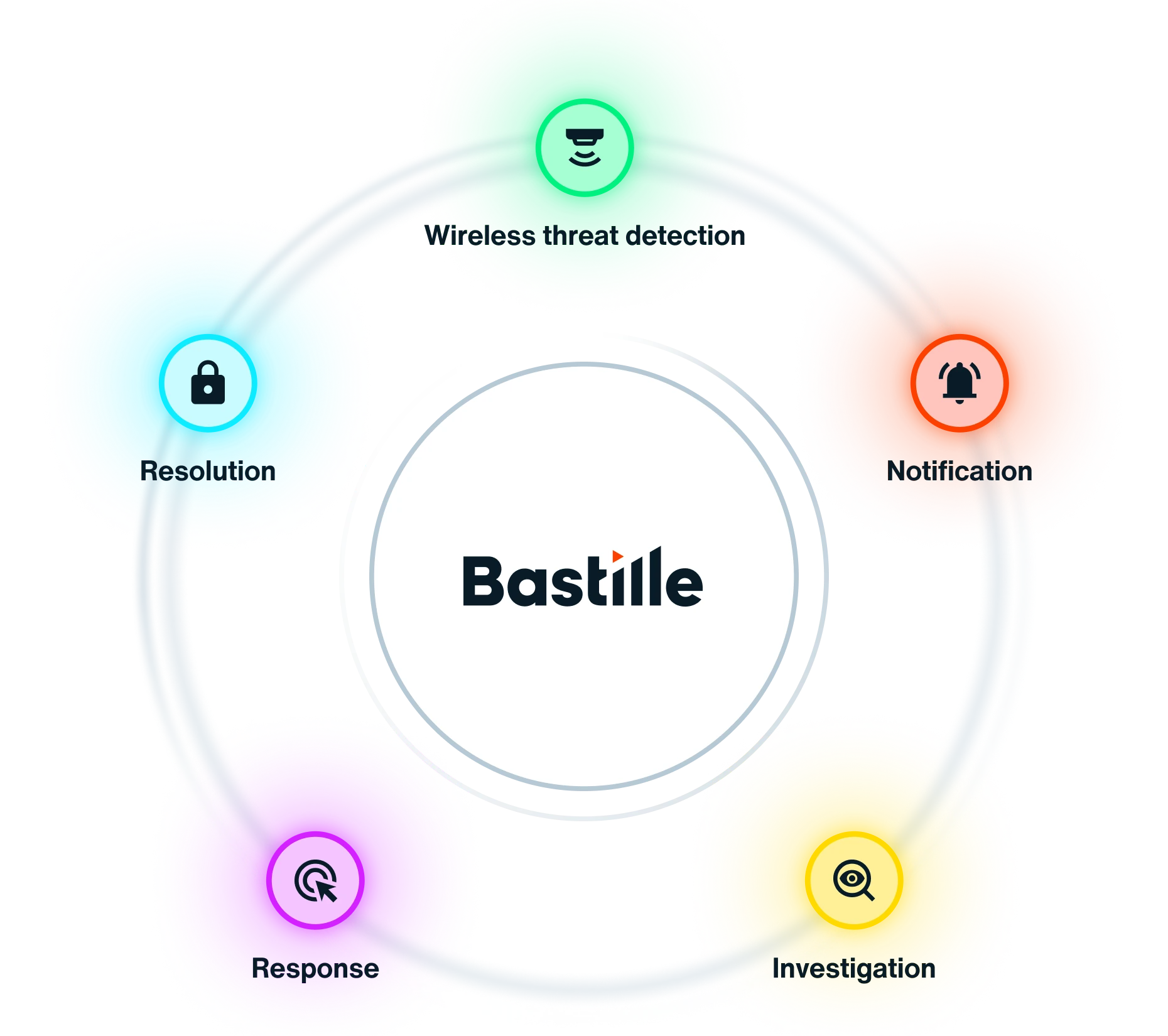
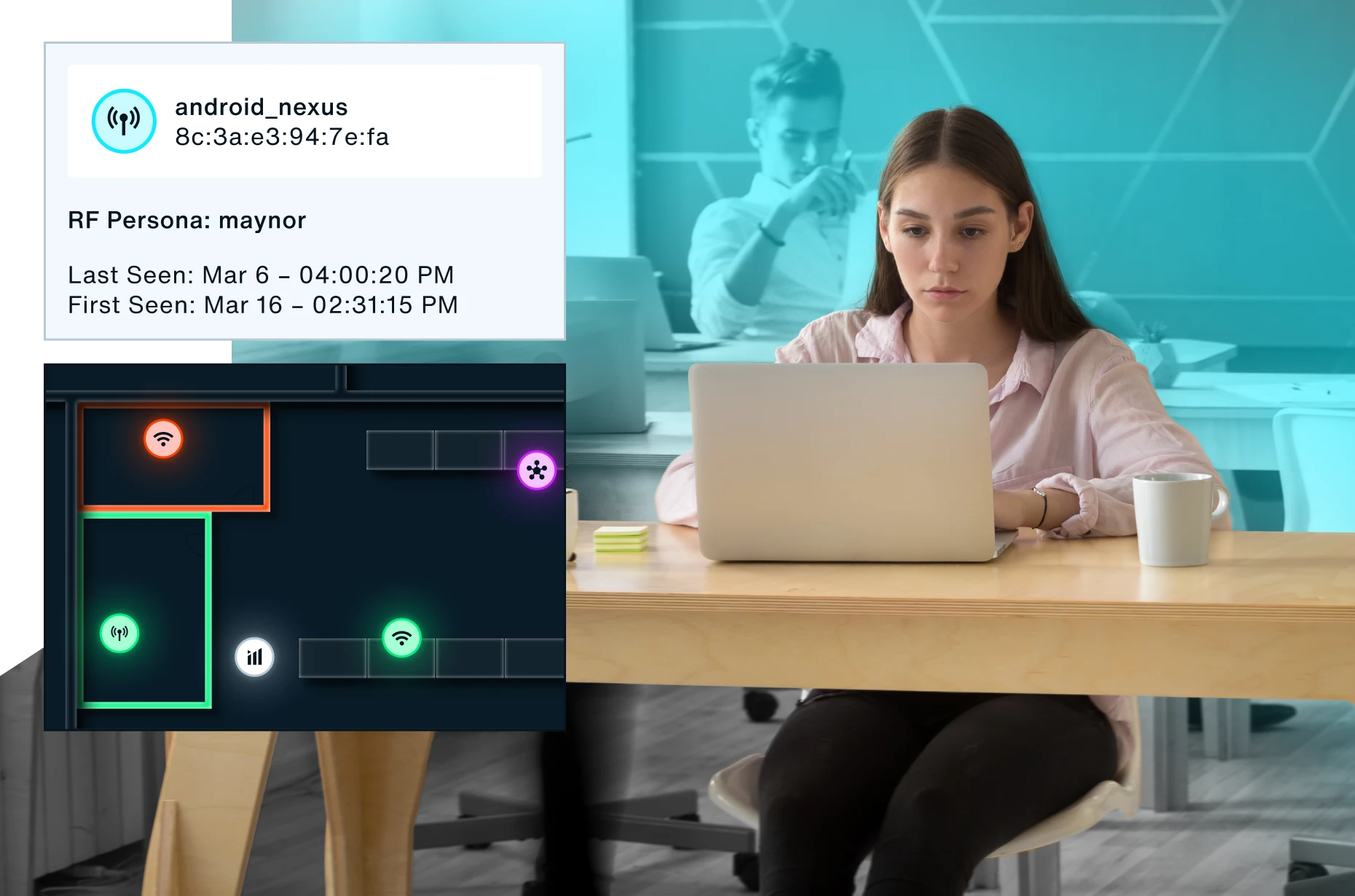
Extend the value of your cybersecurity investments by connecting Bastille to your existing security and threat detection tools. From vulnerable Bluetooth devices to rogue access points, Bastille uncovers a wealth of wireless security data you’ll never want to miss again.