One centralized view of your wireless landscape
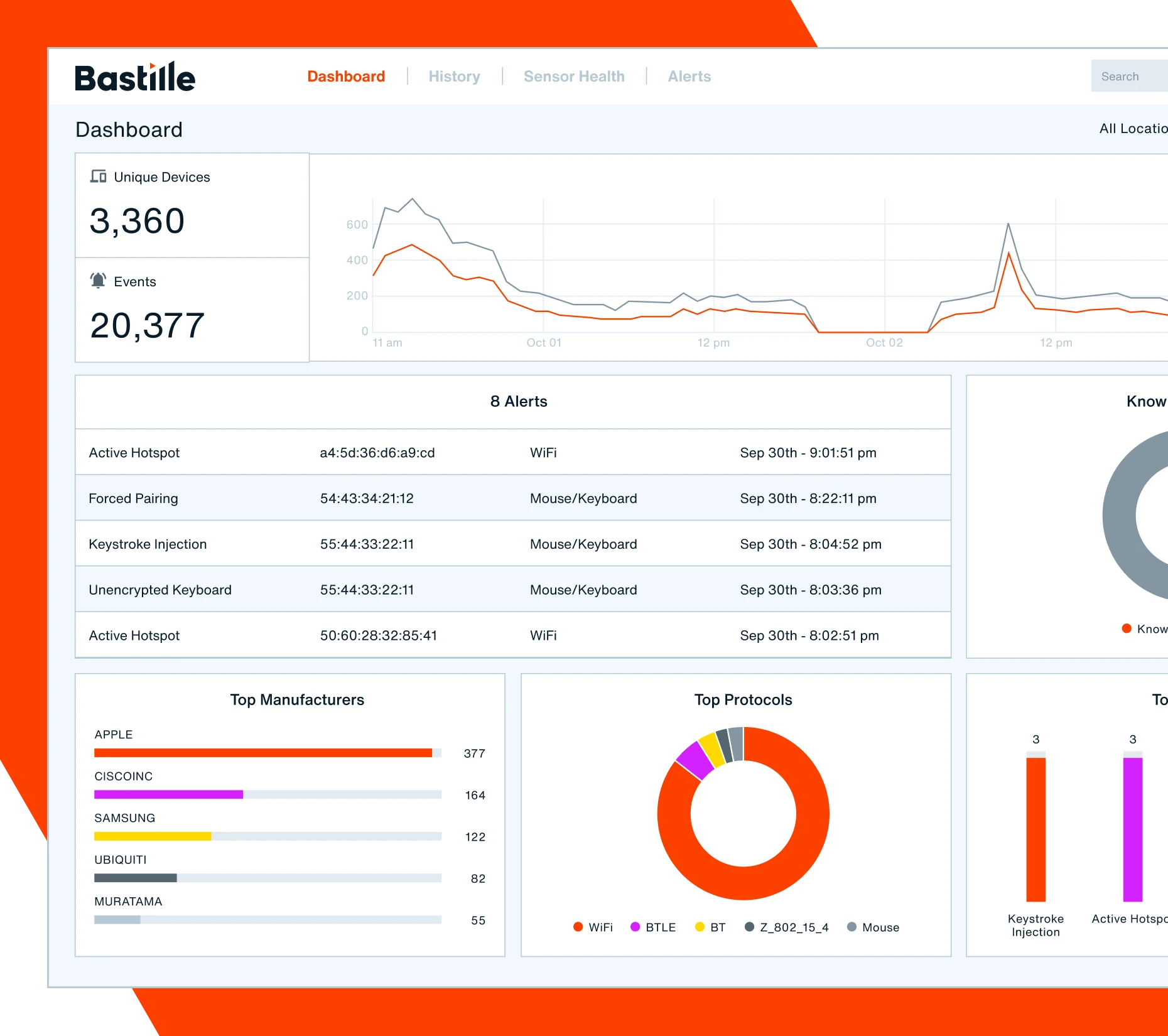
Get ahead of wireless threats and stay audit-ready with a complete inventory of wireless devices and networks across your facilities, all from your Bastille Fusion Center.
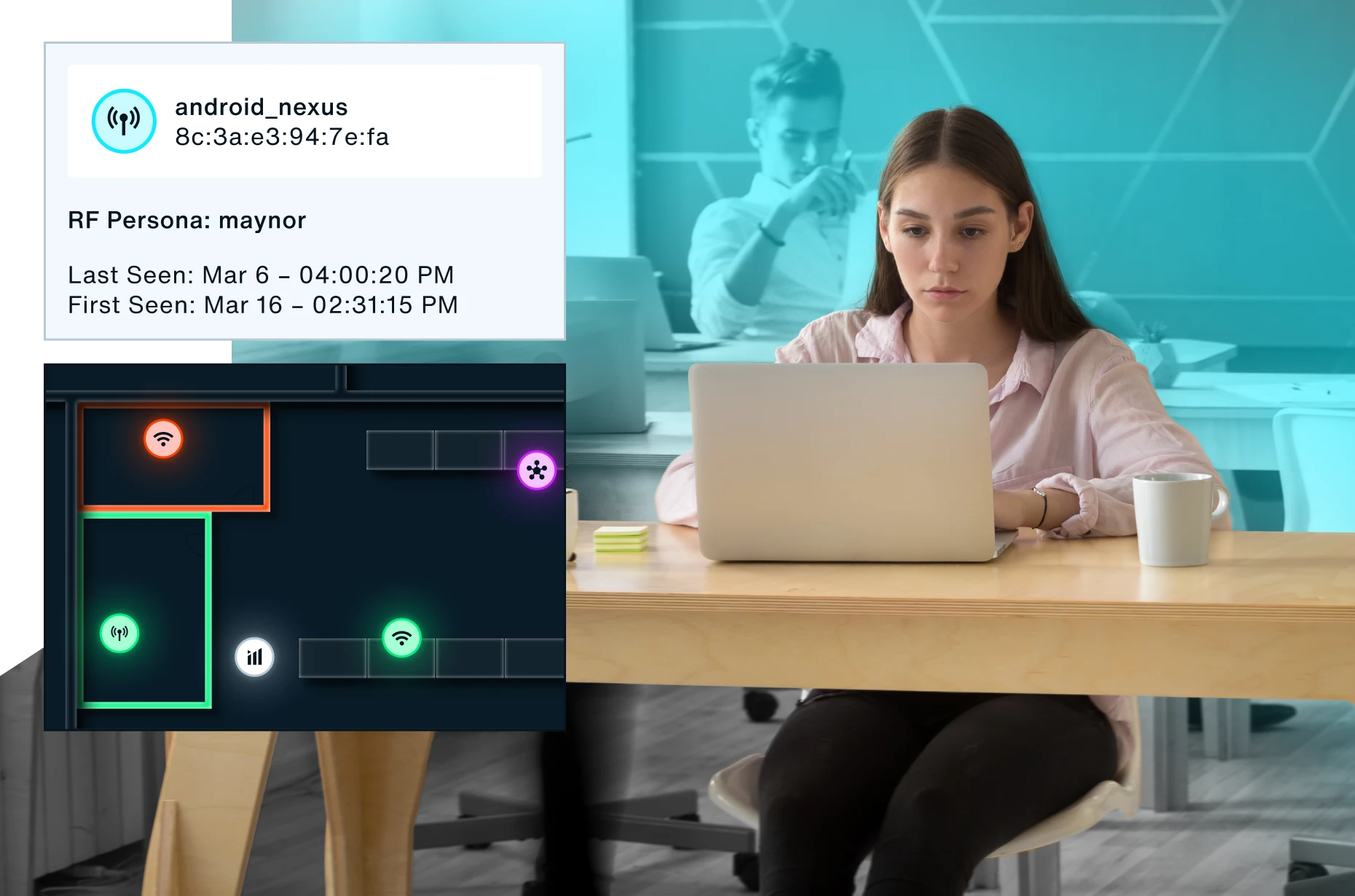
- Access a live catalog of wireless assets with granular network and device details.
- Pinpoint the location and play back the historical position of every wireless device.
- Get alerted of potential threats and view them based on priority.
- View AI-powered, contextual data around device behavior.
- Deep-dive into wireless forensic data after an incident.