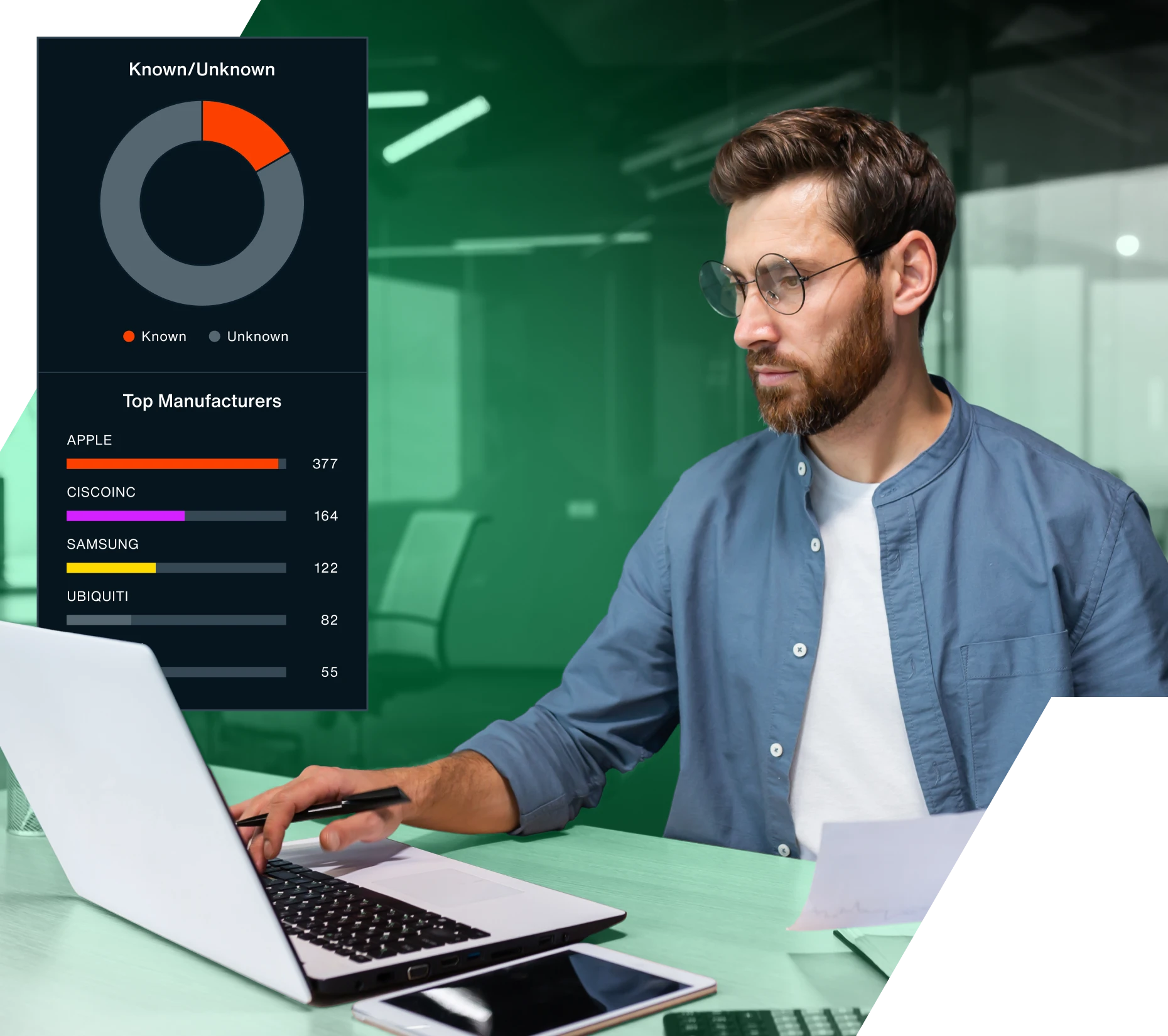
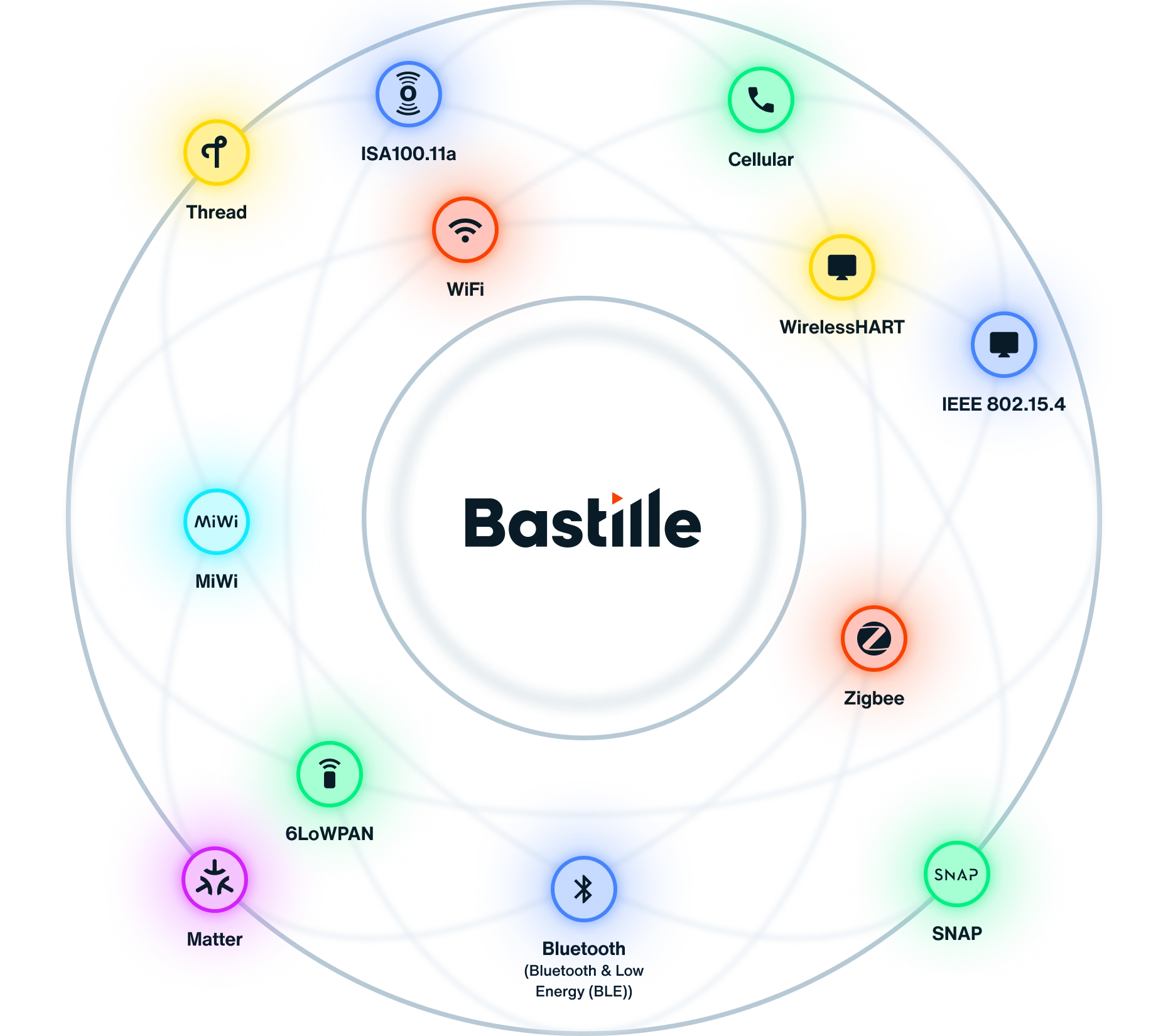
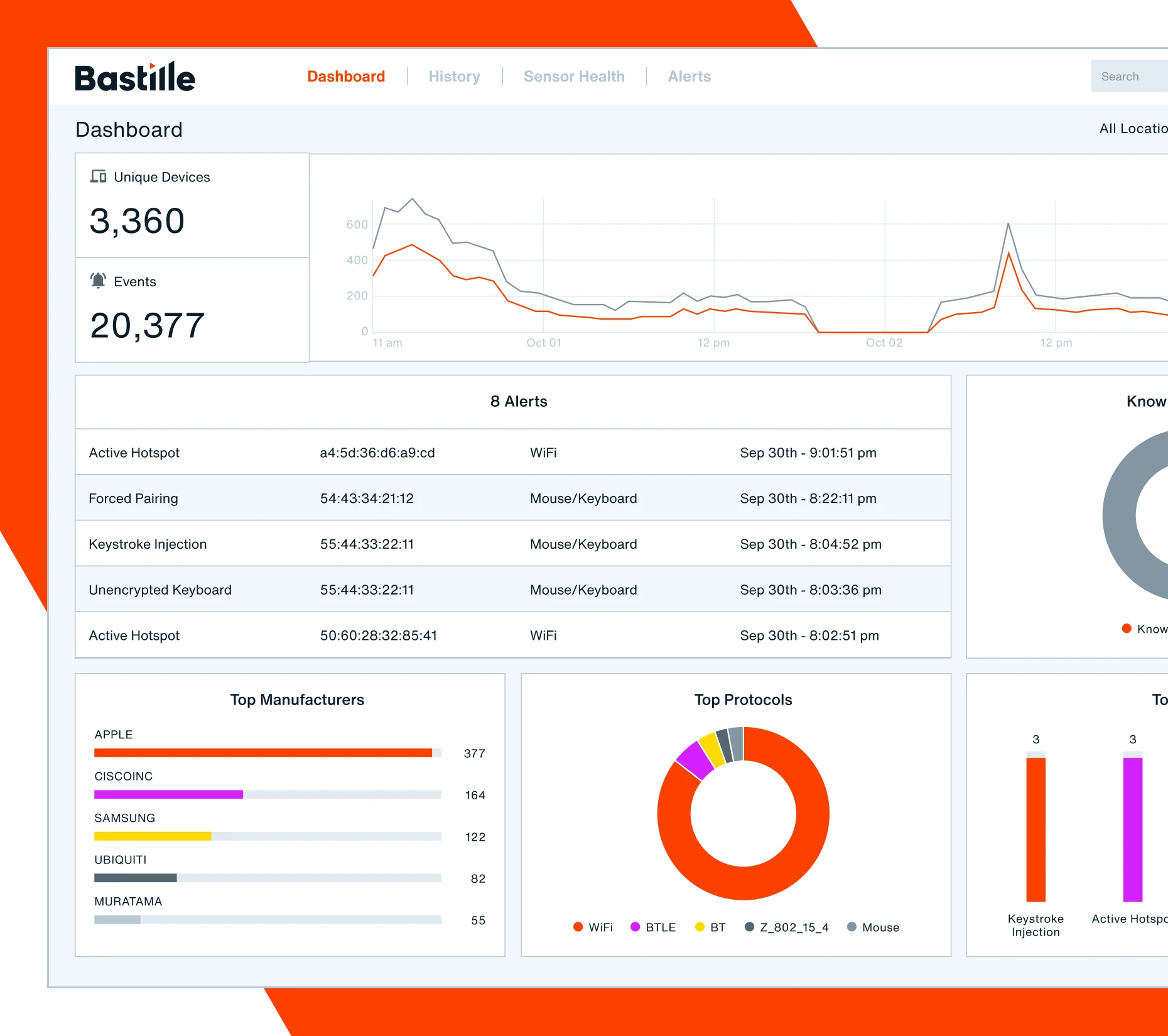
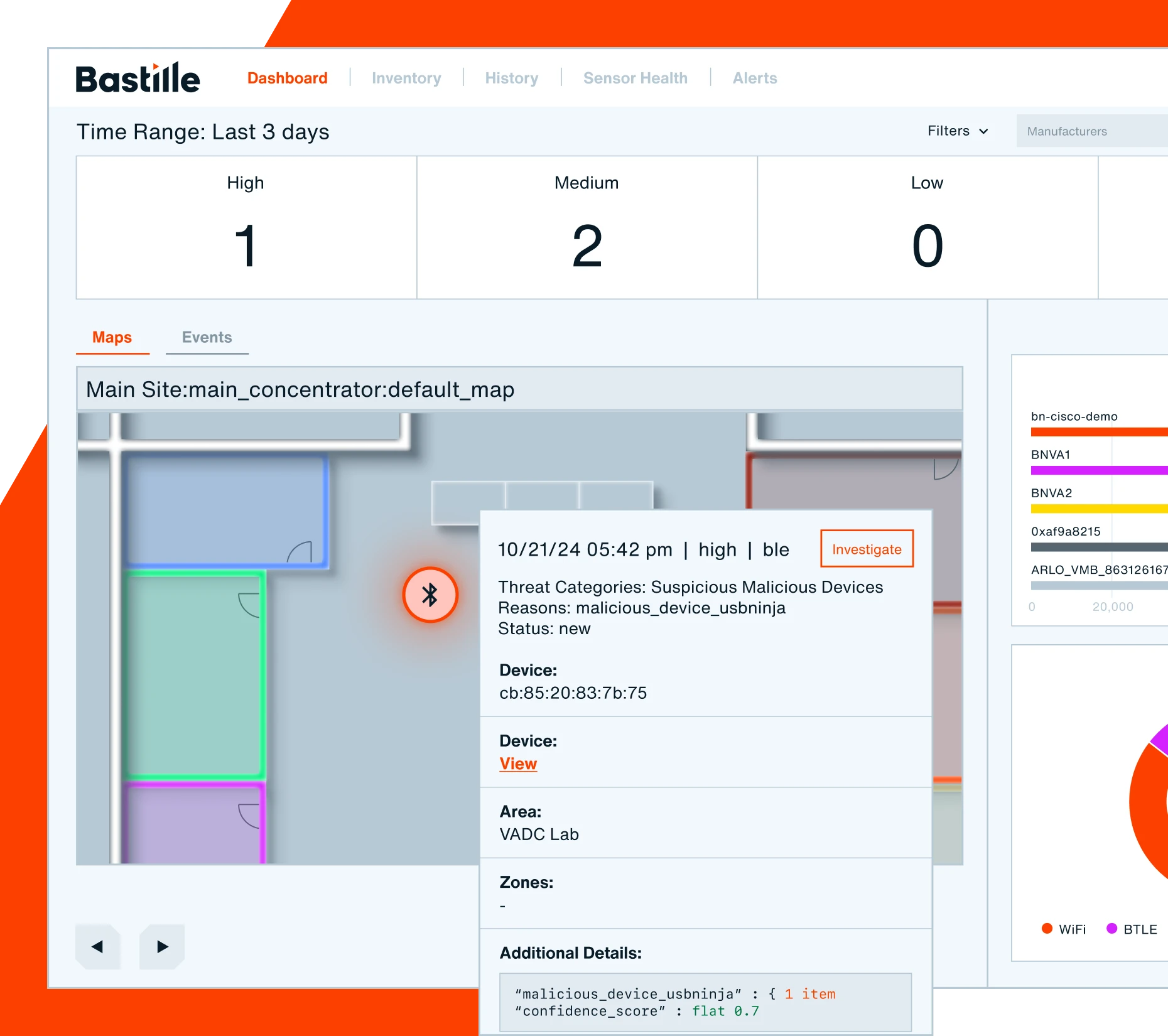
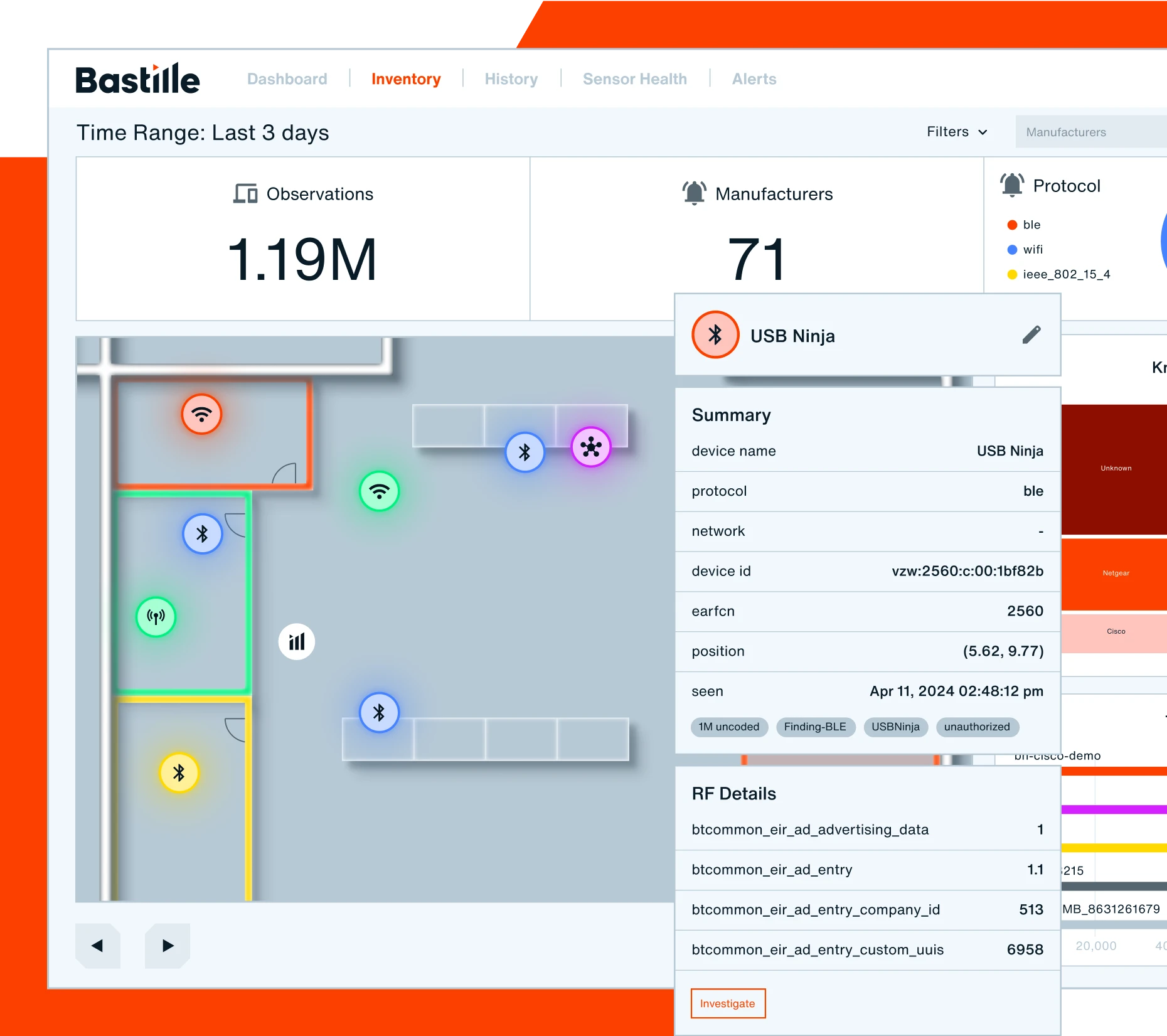
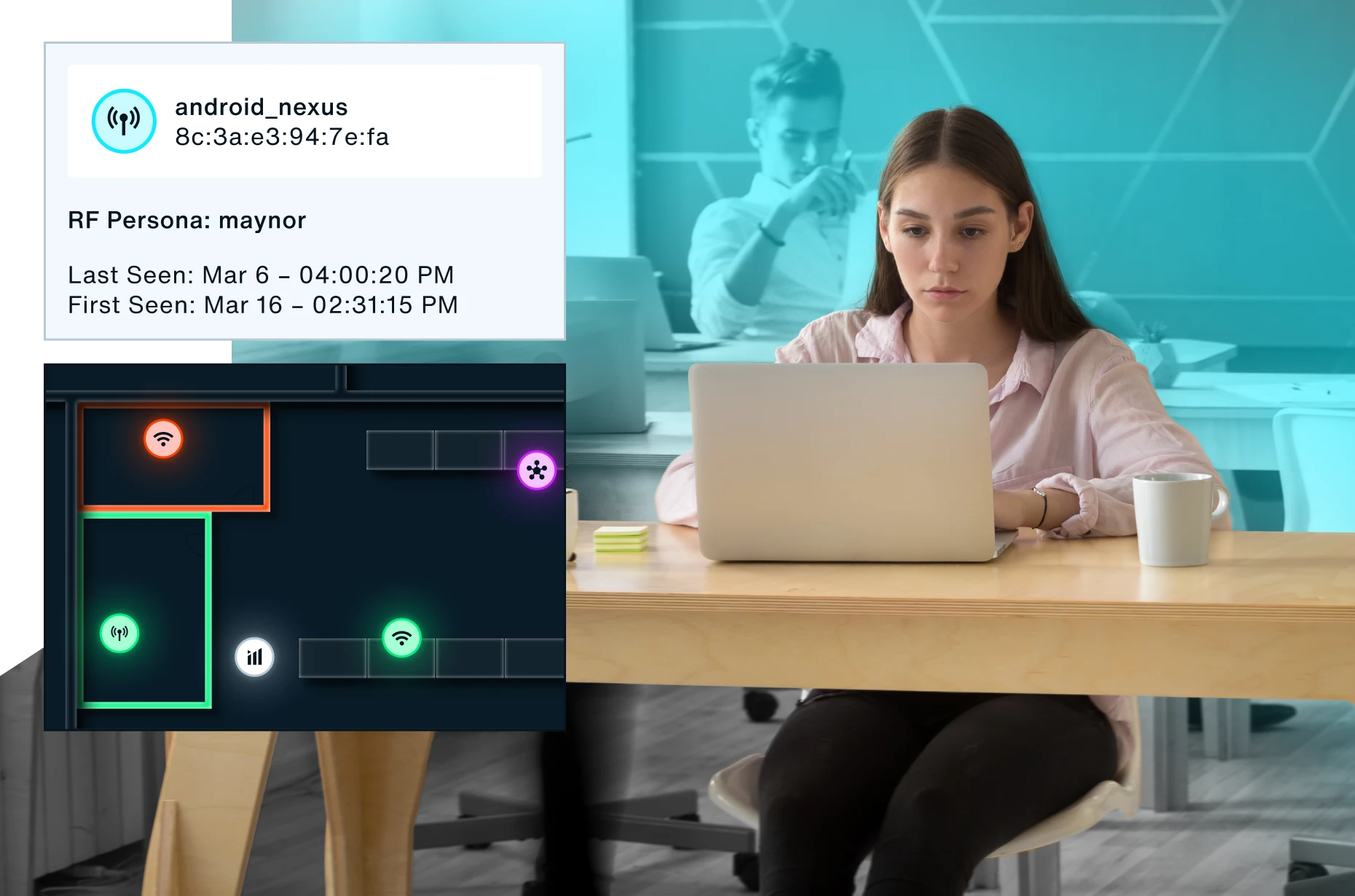
A platform built for cybersecurity resilience
Proactively manage risk and rapidly mitigate wireless threats across the organization with a platform that illuminates on vulnerabilities typically overlooked in a Zero Trust framework. Bastille fits seamlessly into your greater cybersecurity strategy, with scalable API-led architecture and real-time, augmented data streams that integrate with your CAASM and XDR solutions.