Wireless airspace defense for Zero Trust excellence
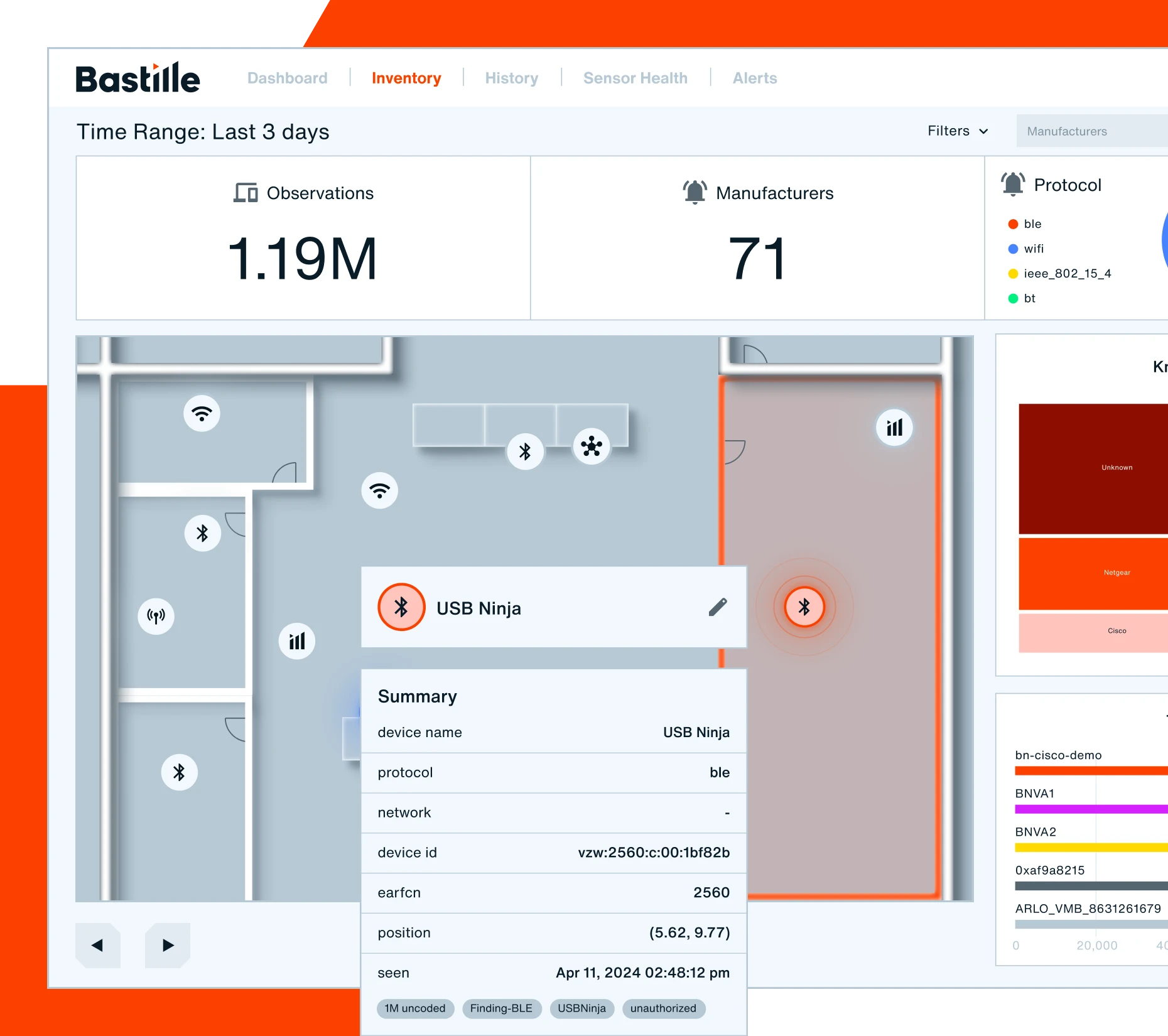
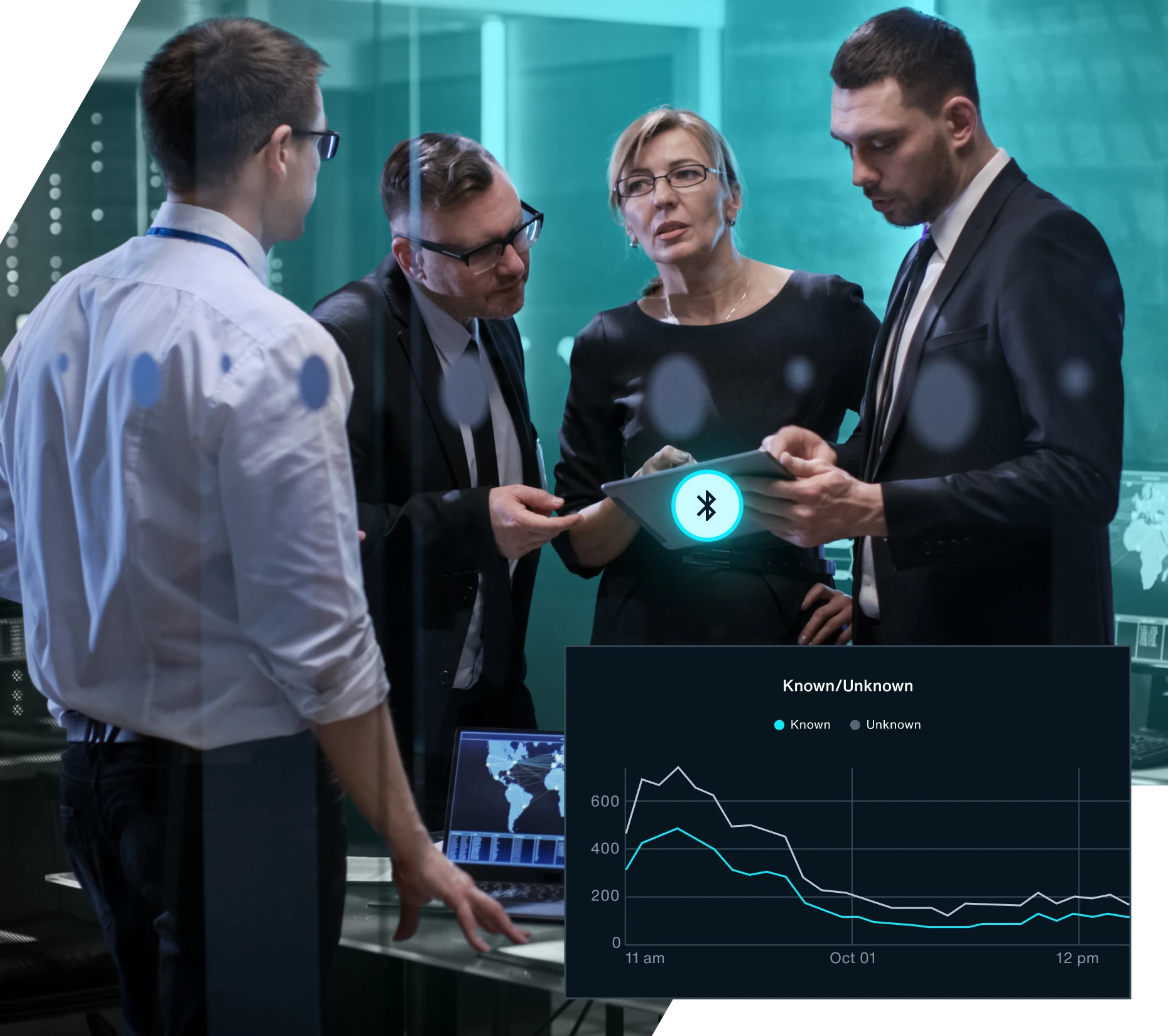
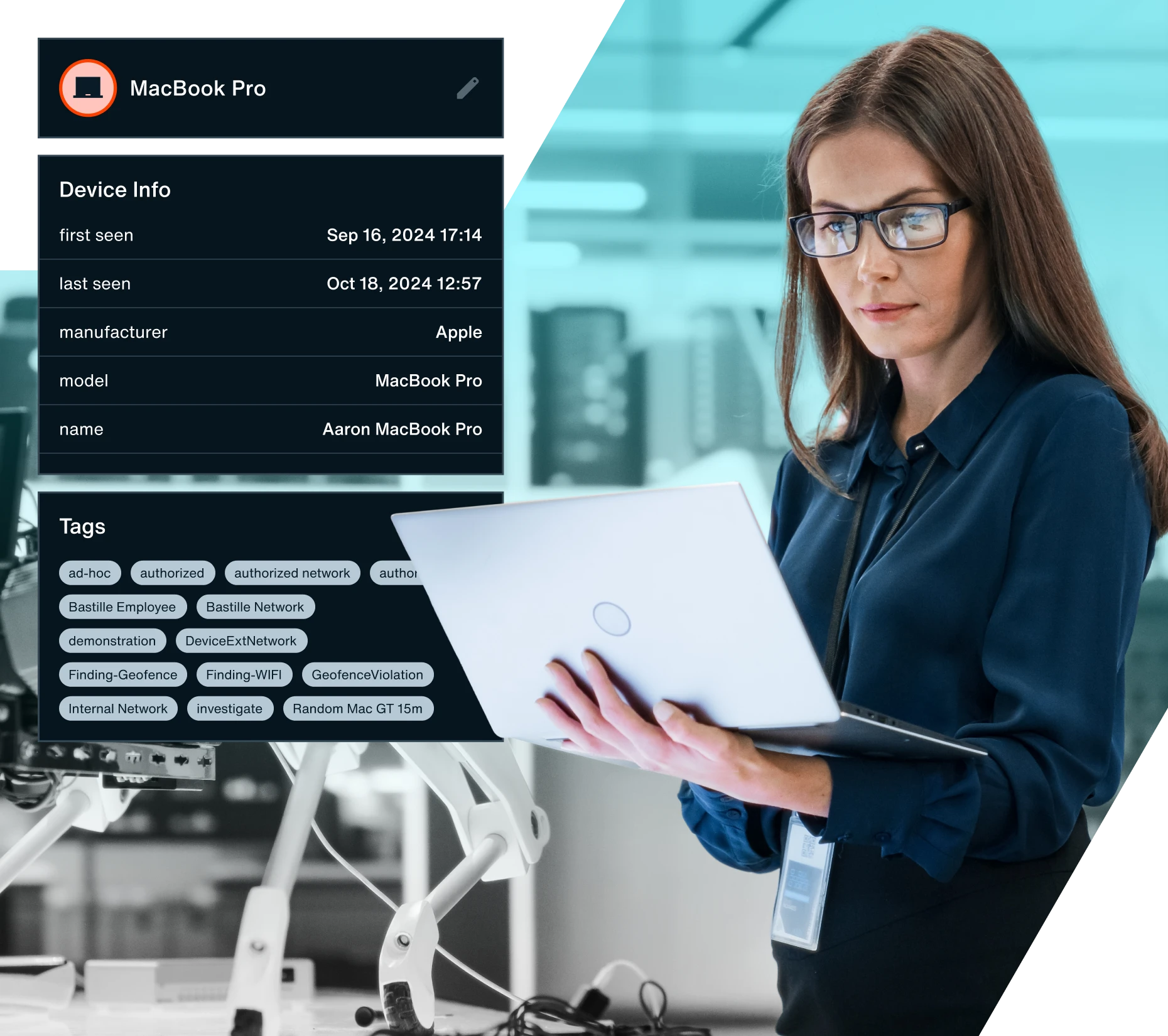
Secure any indoor, outdoor, or temporary event space from malicious attempts at espionage, data exfiltration, and insider threats. Bastille helps agencies meet stringent compliance standards, safely adopt flexible device policies, and stay ahead of today’s sophisticated wireless threats by continuously monitoring government facilities for wireless devices and networks.